
(For Product Managers) Understanding the Basics of LLM and Planning LLM-based Services
arigaram
$77.00
Beginner / NLP, gpt, AI, ChatGPT, LLM
3.9
(7)
Explains why LLMs are needed, their technical background, and basic concepts.
Beginner
NLP, gpt, AI
This lecture is designed to be easily understood even if you have no prior knowledge of Secure Coding. After covering fundamental secure coding concepts, it focuses on web service security. This course was originally conducted as a special lecture hosted by OO University. It provides over 160 source codes with extensive comments, pinpointing core topics and techniques that can be applied immediately in the field.
91 learners
Level Basic
Course period Unlimited



Recommend Course to grow and earn commission!

Marketing Partners
Recommend Course to grow and earn commission!
You can gain a comprehensive understanding of secure coding.
You can learn web security, authentication and authorization, and code review methods for security.
You can learn about security vulnerabilities and countermeasures for each language.
The course is currently in the process of being completed. There is a downside in that you may have to wait a long time until it is fully finished (though I will be adding supplements frequently). Please take this into consideration when making your purchase decision.
January 22, 2026
I have uploaded videos explaining all the code up to Section 12. I will also gradually upload explanation videos for the code in the remaining sections (13 - 19).
September 18, 2025
I have added the precautions and change history to the detailed description page.
In modern software development, security is a necessity, not an option. This course allows you to systematically learn and practice secure coding techniques, a core competency for developing secure software. Designed for all IT professionals interested in security—including developers, security managers, and QA engineers—this course is ideal for security training. (Keywords: security training, penetration testing, security)))
Chapter 1. Orientation
Chapter 2. The Three Elements of Information Security
Chapter 3. The Role of Security in Software Development
Chapter 4. Case Study: Analysis of Famous Security Incidents
Chapter 5. Concept of Threat Modeling
Chapter 6. Introduction to the STRIDE Model
Chapter 7. Introduction to the DREAD Model
Chapter 8. Threat Modeling Tools
Chapter 9. Lab: Threat Modeling Application Examples
Chapter 10. Secure Coding Standards (CERT, OWASP, etc.)
Chapter 11-1. Secure Coding Guidelines
Chapter 11-2. Input Validation and Writing Clean Code
Chapter 11-3. Practice: Writing Secure Input Handling Code
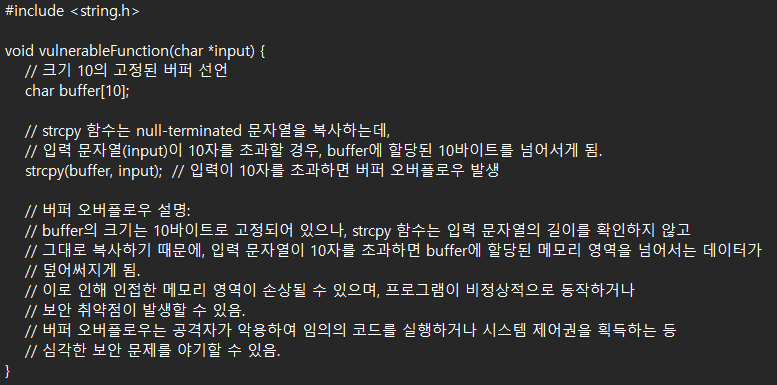
Chapter 12. Security Vulnerabilities in C/C++
Chapter 13. Security Vulnerabilities in Java
Chapter 14. Security Vulnerabilities in Python
Chapter 15. Memory Management and Buffer Overflow
Chapter 16. Format String Vulnerability
Chapter 17. Practice: Writing Secure Memory Management Code
Chapter 18. Object Serialization and Security
Chapter 19. SQL Injection and Countermeasures
Chapter 20. Lab: Writing SQL Injection Defense Code
Chapter 21. Dynamic Typing and Security
Chapter 22. Security Issues with the Pickle Module
Chapter 23. Lab: Writing Secure Data Serialization Code
Chapter 24. Importance of Web Security
Chapter 25. OWASP Top 10 Overview
Chapter 26. XSS Concepts and Types
Chapter 27. XSS Defense Techniques
Chapter 28. Practice: Writing XSS Vulnerability Defense Code
Chapter 29. CSRF Concepts and Attack Methods
Chapter 30. CSRF Defense Techniques
Chapter 31. Practice: Writing CSRF Defense Code
Chapter 32. How to Configure Security Headers
Chapter 33. Importance and Configuration of HTTPS
Chapter 34. Differences between Authentication and Authorization
Chapter 35. Secure Authentication Methods
Chapter 36-1. Understanding Passwords and Salt
Chapter 36-2. Secure Password Storage Techniques
Chapter 37. Practice: Password Management through Hashing and Salting
Chapter 38. OAuth Concepts and Use Cases
Chapter 39. Concepts and Usage of JWT (Java Web Token)
Chapter 40. Implementing Authentication with JWT
Chapter 41. Secure Session Management Techniques
Chapter 42. Session Hijacking Prevention Methods
Chapter 43. The Importance of Code Review
Chapter 44. Utilization of Static Analysis Tools
Chapter 45. Concepts of Dynamic Analysis
Chapter 46-1. Pentest (Penetration Testing) Tools
Chapter 46-2. Penetration Testing Stages
Chapter 47. Hands-on: Simple Pentest Simulation
Over 160 richly commented code examples are provided.
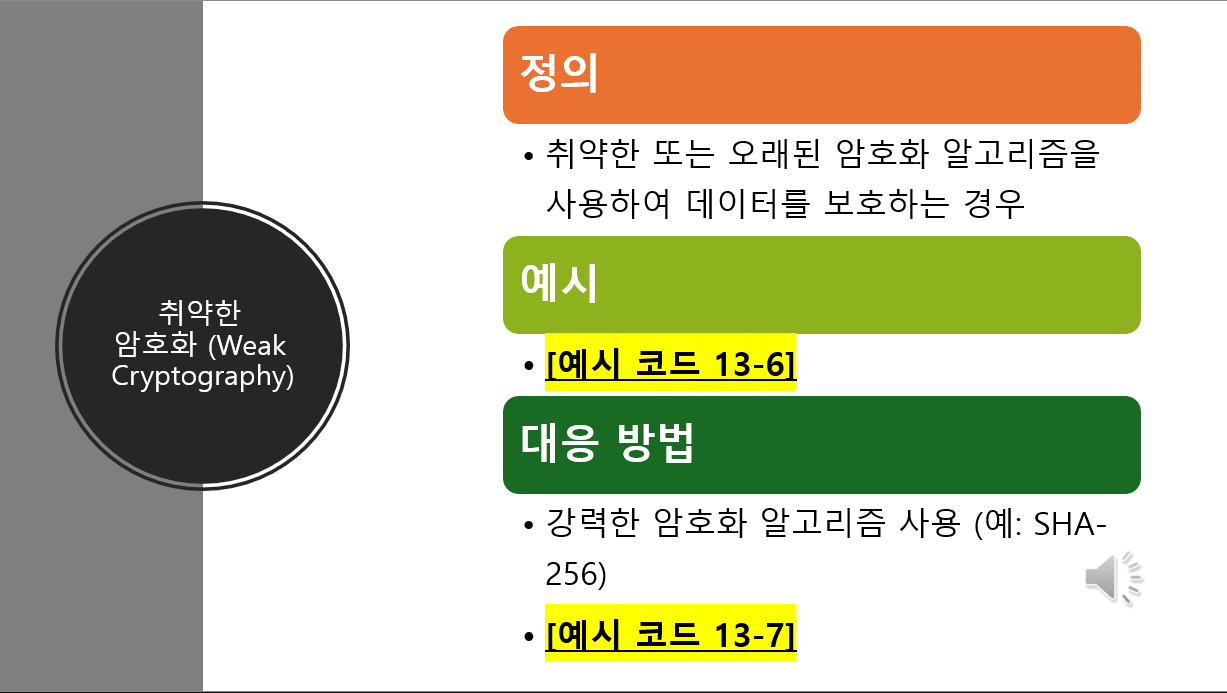
Both vulnerable and patched code are presented together. Detailed countermeasures for addressing vulnerabilities are provided, making them directly applicable to real-world practice.
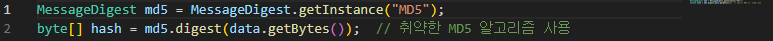
For example, Example Code 13-6 contains vulnerable code.
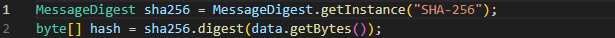
Meanwhile, Example Code 13-7 contains the code with the vulnerabilities addressed.
Acquiring basic principles and practical skills for writing secure code
Acquiring understanding and response capabilities for language- and platform-specific security vulnerabilities
Strengthening response capabilities for major threats related to web security and authentication/authorization
Acquire practical knowledge to establish a security culture within development organizations
Prevention is the best defense against security incidents. Start now.
Take your first step toward secure coding with this course!
Who is this course right for?
Someone who wants to know what secure coding is
Those who want to build a strong foundation in secure coding
Those who need to fix web application vulnerabilities immediately
Someone who wants to learn techniques for immediate practical application.
Need to know before starting?
It is helpful to have an understanding of one or two languages among C, Java, Python, and Javascript.
626
Learners
31
Reviews
2
Answers
4.5
Rating
18
Courses
I am someone for whom IT is both a hobby and a profession.
I have a diverse background in writing, translation, consulting, development, and lecturing.
All
209 lectures ∙ (22hr 39min)
Course Materials:
All
8 reviews
5.0
8 reviews
Reviews 2
∙
Average Rating 5.0
Reviews 2
∙
Average Rating 5.0
Reviews 3
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
Check out other courses by the instructor!
Explore other courses in the same field!
$77.00