
취미로 해킹#2(해커의 컴퓨팅)
장용하
이제 사이버 공간에서 이전보다 더 많은 자유를 누리실 수 있습니다.
입문
모의해킹
You can clear all preliminary challenges of the hacking competition DIMICTF (2019).

How to find and understand security vulnerabilities related to portable, reversing, web, and mask areas.
Computer science knowledge relevant to each challenge.
How to install and use security tools.
Hacking as a hobby, hacking as a hobby.
※ "Hacking as a Hobby" content only focuses on legal hacking to contribute to a safe information security ecosystem.

< To view the course content in book form: Paper book/e-book (link) >
Here, we'll master the 2019 DIMICTF Preliminary Challenge (which is said to be more difficult than the final). We'll practice every challenge from start to finish.
DIMICTF is sponsored by the Ministry of Science and ICT and the Korea Information Technology Research Institute.
This is a domestic hacking competition hosted and organized by Korea Digital Media High School.
If you master all the course content, you will be able to solve challenges that the winning team couldn't, and as your skills improve, you will be able to challenge yourself in more difficult hacking competitions in the future.
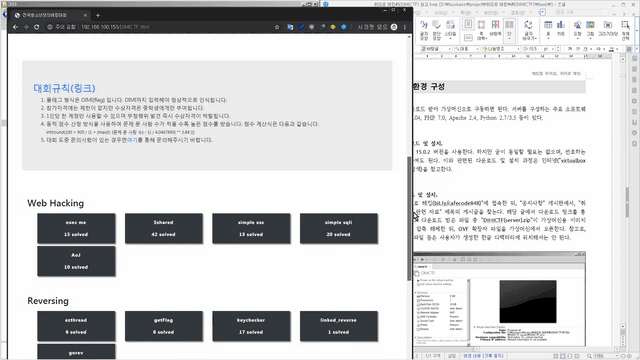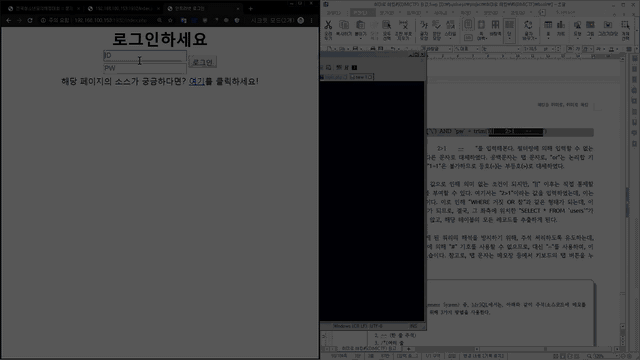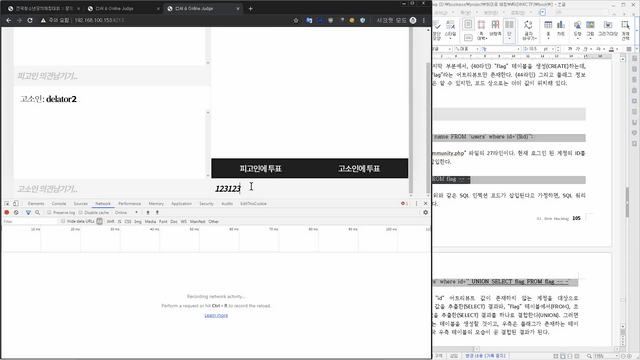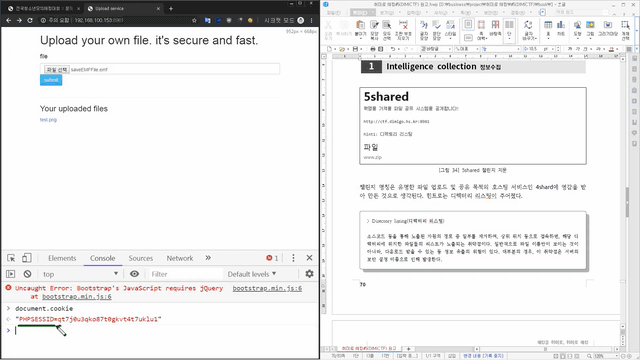
Hacking competitions cover four main areas: the portable area, which involves system hacking and primarily aims to seize authority ; the reversing area, which involves disassembling software and searching for key information hidden somewhere inside, like a treasure hunt ; the web area, which involves bypassing a website's lax security procedures to extract key information; and the mask area, where vulnerability detection is more important than specific knowledge.
You will learn about finding Easter eggs that developers have secretly hidden, uploading files with specific extensions that are blocked from being uploaded, creating attack codes one by one in machine language , invading inaccessible memory areas to trigger unplanned functions, restoring obfuscated software to its original state, and injecting various special characters in combinations into user-interactive areas such as login pages to activate hidden functions .
By practicing various challenges that incorporate the above content, you will learn how to identify and address vulnerabilities . Specifically, the course includes theory and practice on bugs and vulnerabilities related to the keywords mentioned in the image below. 
To ensure effective learning, we provide a virtual image that recreates the actual competition situation . This allows you to practice as if you were participating in the competition. We also cover how to install and use tools. Tools used include Ghidra, GDB-PEDA, JD-GUI, Checksec, and Uncompyle6.
The lecture focuses on minimizing individual learning by discussing both phenomena and principles, but if you have any questions, please use the Q&A board on the Naver Cafe "Hacking as a Hobby (link) ".
For further details, please refer to the prologue video, which contains answers to the questions below.
▶ What is an effective way to study?
▶ How is the lecture conducted?
▶ What is your relationship with "Hacking as a Hobby #1-4"?
▶ What are the differences from other courses?
Who is this course right for?
Anyone who wants to complete all preliminary challenges of the hackathon DIMICTF.
Anyone who wants to learn hacking little by little as an academic hobby.
Anyone who wants to participate in more difficult hacking competitions.
Students in related departments who need to supplement their major knowledge.
Those who wish to pursue a career in information security.
Need to know before starting?
If you have experience writing C or Python programs, it may be helpful.
11,713
Learners
995
Reviews
118
Answers
4.7
Rating
9
Courses
ㆍ 정보보안기사
ㆍ "생활코딩! 파이썬" 도서 저자
ㆍ "취미로 해킹#N" 도서(+강의) 저자
ㆍ 한국외국어대학교 정보보안 담당 직원
ㆍ 미사일전략사령부 CERT 팀장(육군 학사#59)
ㆍ 한국공학대학교 컴퓨터공학 학사(4.42)
All
96 lectures ∙ (13hr 16min)
1. 1. Prologue
03:34
4. 4. Mic Check
05:51
5. 5. dimi-math 1
06:29
6. 6. dimi-math 2
08:00
7. 7. dimi-math 3
08:02
8. 8. reader 1
06:43
9. 9. reader 2
10:32
12. 12. CTFind 1
08:35
13. 13. CTFind 2
06:31
14. 14. CTFind 3
07:55
15. 15. exec me 1
04:34
16. 16. exec me 2
07:59
17. 17. 5shared 1
08:41
18. 18. 5shared 2
05:40
19. 19. 5shared 3
07:02
20. 20. simple xss
11:20
23. 23. AoJ 1
07:52
24. 24. AoJ 2
06:55
25. 25. AoJ 3
09:48
26. 26. ezheap 1
06:23
27. 27. ezheap 2
05:35
28. 28. ezheap 3
05:56
29. 29. ezheap 4
06:30
30. 30. ezheap 5
08:02
31. 31. ezheap 6
09:02
32. 32. ezheap 7
08:16
33. 33. ezheap 8
12:05
34. 34. ezheap 9
09:53
35. 35. ezheap 10
07:05
36. 36. ezheap 11
08:19
37. 37. ezheap 12
12:23
54. 54. dimi-farm 1
08:31
55. 55. dimi-farm 2
10:06
56. 56. dimi-farm 3
08:53
57. 57. dimi-farm 4
07:25
58. 58. dimi-farm 5
08:58
59. 59. dimi-farm 6
09:18
60. 60. dimi-farm 7
07:45
61. 61. dimi-farm 8
05:02
62. 62. dimi-farm 9
07:40
63. 63. dimi-farm 10
06:48
64. 64. dimi-farm 11
10:09
65. 65. dimi-farm 12
05:40
66. 66. dimi-login 1
06:52
67. 67. dimi-login 2
06:08
68. 68. dimi-login 3
07:36
69. 69. dimi-login 4
10:53
70. 70. dimi-login 5
09:34
71. 71. dimi-login 6
08:22
72. 72. dimi-login 7
10:45
73. 73. dimi-login 8
09:40
74. 74. dimi-login 9
10:17
All
18 reviews
4.9
18 reviews
Reviews 2
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
Reviews 2
∙
Average Rating 5.0
Reviews 7
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
$42.90
Check out other courses by the instructor!
Explore other courses in the same field!