
Hacking as a hobby #2 (hacker's computing)
caliber50
You now have more freedom in cyberspace than ever before.
Beginner
Penetration Testing
We will cover all the challenges in Nebula, a wargame that will help you develop your system hacking skills, from start to finish, including setting up a practice environment. You will also learn the computer science knowledge required for each challenge.
491 learners
Level Basic
Course period Unlimited

Reviews from Early Learners
5.0
SEOYEON_KIM
First of all, the voice is good and the explanation is good. Haha It's not hard to follow. Since it's done through a war game, it's less burdensome and the decisive thing is fun.
5.0
rini9
It was a good lecture.
5.0
whopdo
I heard it well
Primarily the ability and intuition to discover system-related vulnerabilities.
Computer science knowledge relevant to each challenge.
Hacking as a hobby, hacking as a hobby.
※ "Hacking as a Hobby" content only focuses on legal hacking to contribute to a safe information security ecosystem.

< To view the course content in book form: Paper book/e-book (link) >
Here, we'll master the popular wargame Nebula . Based on fully translated Korean materials, we'll practice every challenge from start to finish.
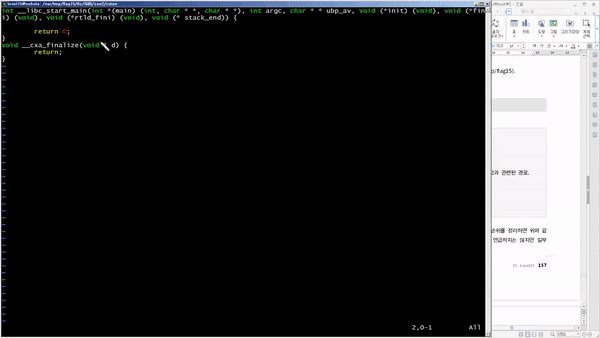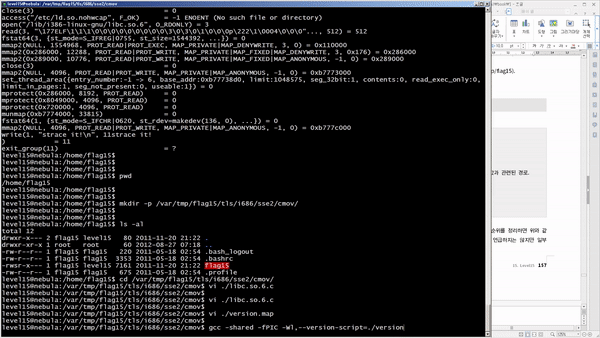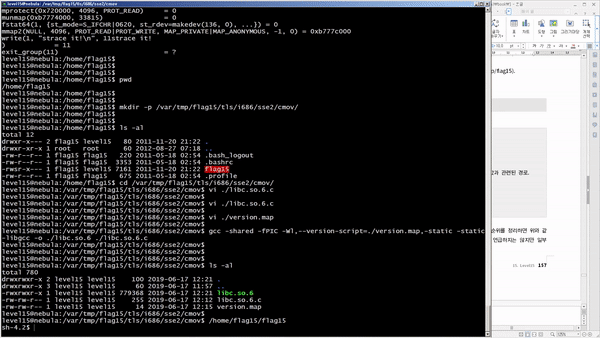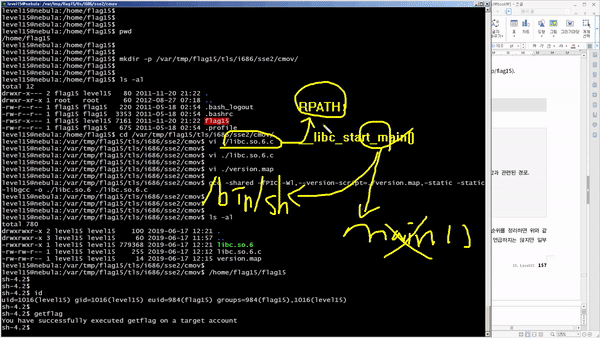
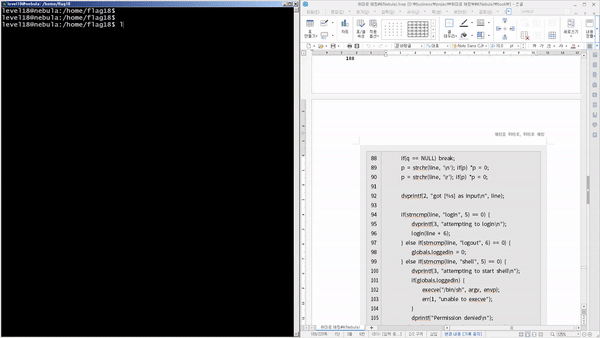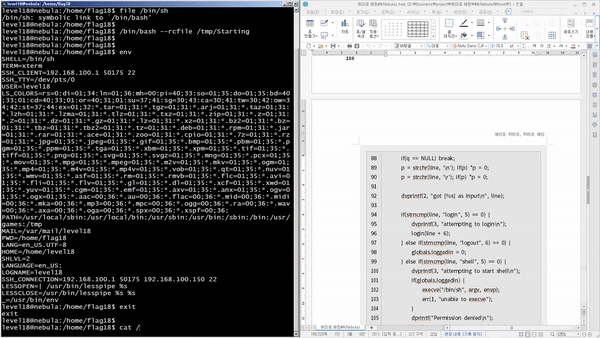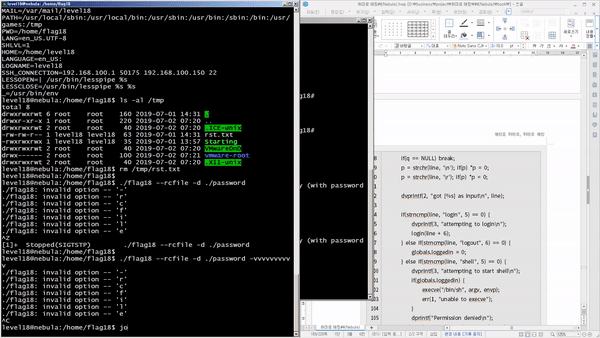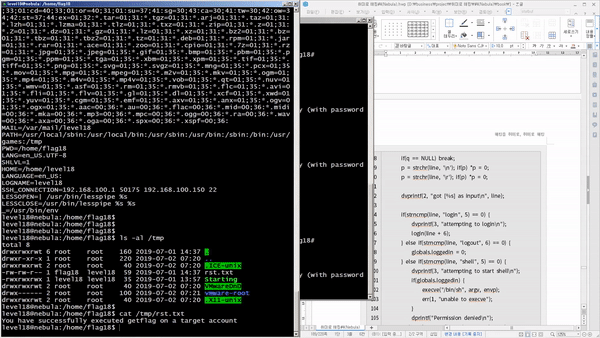
We'll discover and exploit vulnerabilities in Linux systems, widely used as servers , and gradually escalate privileges . Through this, you'll discover that most vulnerabilities are the result of mistakes made by developers who lack security knowledge . You'll witness programs that become hostile due to competition. You'll witness how poor data filtering can lead to program collapse . You'll witness how abuse of privileges can lead to outside interference . You'll also witness how poorly applied security knowledge can lead to certain functions being replaced with others .
You'll learn how to discover and mitigate system-related security vulnerabilities through a variety of scenarios. Specifically, you'll cover theory and practice on vulnerabilities related to permissions (general/special), relative paths, environment variables, input filtering, schedulers, password hashes, code injection, cleartext communication, legacy open source, race conditions, variable initialization, library hooking, data encryption, file attributes, deserialization, permission checks, and exception handling.
[Q1] I didn't take "Hacking as a Hobby #1-3." Is it okay to start from here?
[Ans] If you have at least basic Linux system skills (connection, compilation, navigation, text editing, etc.) , this shouldn't be a problem. If you don't, we recommend separate learning or taking the most relevant course, "Hacking as a Hobby #1."
[Q2] What abilities will you acquire when you complete the course?
[Ans] You will learn how to exploit various vulnerabilities in the Linux environment. You will gain more advanced skills in addressing the aforementioned vulnerabilities than before, enabling you to develop more secure programs. Additionally, the extensive source code analysis included will be helpful for future reversing challenges.
Who is this course right for?
For those who want to complete all the content of Wargame Nebula.
Anyone who wants to learn hacking little by little as an academic hobby.
Anyone who wants to participate in domestic/international hacking competitions in the future.
Students in related departments who need to supplement their major knowledge.
Those who wish to pursue a career in information security.
Need to know before starting?
If you have experience writing C programs, it may be helpful.
11,802
Learners
1,005
Reviews
118
Answers
4.7
Rating
9
Courses
ㆍ Information Security Engineer
ㆍ Author of "Coding Everybody! Python"
ㆍ Author of "Hacking as a Hobby #N" (Book & Lectures)
ㆍ Information Security Officer at Hankuk University of Foreign Studies
ㆍ CERT Team Leader at Missile Strategy Command (Army OCS #59)
ㆍ B.S. in Computer Science and Engineering, Tech University of Korea (4.42 GPA)
All
37 lectures ∙ (6hr 16min)
1. 1. Prologue
01:38
4. 4. level00
14:59
5. 5. level01
21:18
6. 6. level02
12:50
7. 7. level03
11:27
8. 8. level04
14:30
9. 9. level05
07:52
10. 10. level06
06:44
11. 11. level07
16:37
12. 12. level08
13:23
13. 13. level09(1)
12:11
14. 14. level09(2)
10:24
15. 15. level10
15:50
16. 16. level11(1)
10:30
17. 17. level11(2)
10:49
18. 18. level11(3)
08:16
19. 19. level11(4)
11:14
20. 20. level12
11:12
21. 21. level13
09:16
22. 22. level14
11:01
23. 23. level15(1)
09:39
24. 24. level15(2)
08:26
25. 25. level16(1)
11:36
26. 26. level16(2)
09:26
27. 27. level17(1)
07:47
28. 28. level17(2)
10:24
29. 29. level18(1)
09:10
30. 30. level18(2)
09:09
31. 31. level18(3)
10:33
32. 32. level18(4)
15:08
33. 33. level18(5)
06:42
34. 34. level18(6)
07:11
35. 35. level19(1)
07:57
36. 36. level19(2)
11:35
37. 37. Epilogue
01:47
All
19 reviews
4.9
19 reviews
Reviews 1
∙
Average Rating 5.0
Reviews 6
∙
Average Rating 5.0
Reviews 3
∙
Average Rating 3.7
Reviews 5
∙
Average Rating 5.0
Reviews 5
∙
Average Rating 4.8
$26.40
Check out other courses by the instructor!
Explore other courses in the same field!