Linux for Beginners: Mastering the Command Line. The ultimate course for Linux administration in corporate jobs.
Unlock the power of the Linux operating system with this comprehensive beginner-friendly course. Whether new to IT or wanting to advance technical skills, this course will take one from zero to proficient in Linux fundamentals. Learn to navigate the command line, manage files and directories, handle permissions, and automate tasks with shell scripting.
What You'll Learn:
How to Navigate the Linux File System and Master the Command Line
Managing users, groups, and file permissions for secure access
Installing, updating, and removing software with package managers
Basic system administration and troubleshooting skills
With hands-on labs and real-world examples, you’ll quickly build confidence in managing Linux environments. By the end of this course, you’ll have a strong understanding of essential Linux concepts like file permissions, process management, and network configuration.
Also, this course covers basic networking, disk management, and process monitoring. Whether you have a career goal in the realms of DevOps, cybersecurity, or cloud engineering, learn Linux today to make more career opportunities pop open in IT, DevOps, SRE, Support, IT helpdesk, IT Admin, cybersecurity, or software development!
Practical Skills for Self-Confidence on Any Linux-based System
Boost Your Tech Portfolio
![[Eduwill White Hacker] Tracking Cybercrimes Using Hacking (OSINT)Course Thumbnail](https://cdn.inflearn.com/public/courses/330474/cover/dcce6b36-ed1b-48f0-a42b-3cd4fa477dc0/330474-eng.png?w=420)







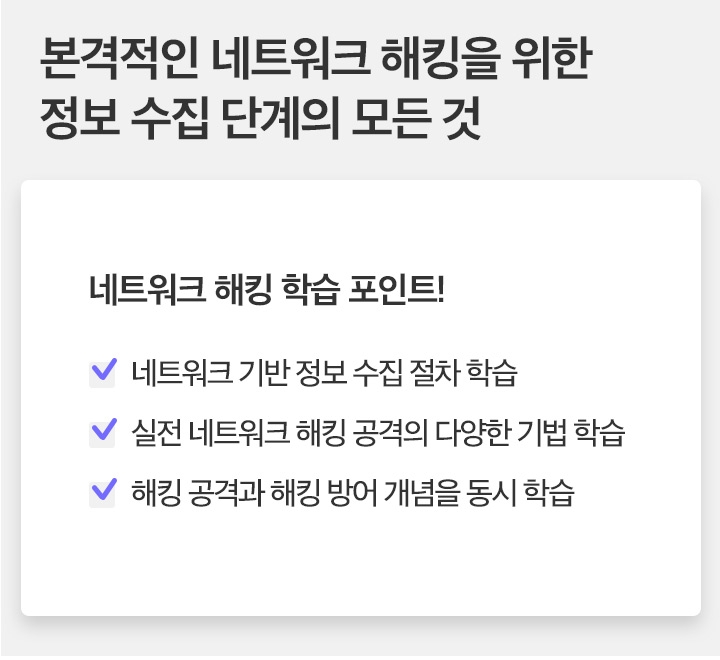


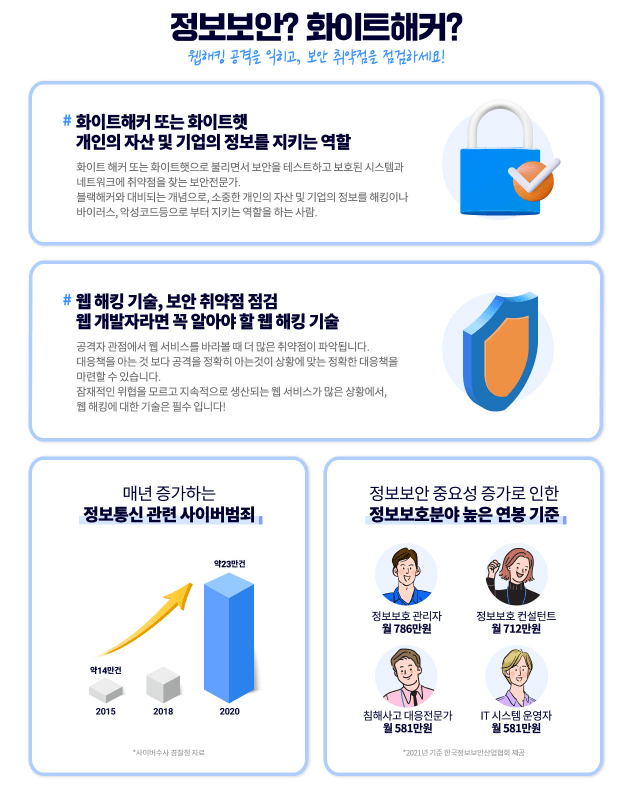
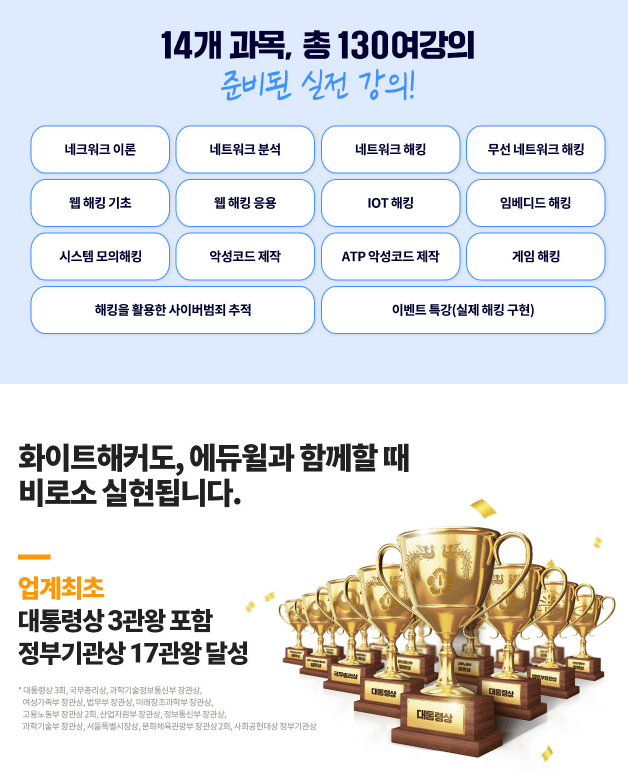

![[Eduwill White Hacker Training Course] System Simulation HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329610/cover/22f513f5-3a82-4c72-8d0e-b6b4d3031d93/329610-eng.jpg?w=420)
![[Eduwill White Hacker] Network AnalysisCourse Thumbnail](https://cdn.inflearn.com/public/courses/329693/cover/4a4b65e9-9621-4884-815b-efbdd604c685/329693-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] Web Hacking Techniques (Basic + Application)Course Thumbnail](https://cdn.inflearn.com/public/courses/330444/cover/f1e3c27c-1528-41b7-b307-ac27a997c1c8/330444-eng.png?w=420)
![[Eduwill White Hacker] Game HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329746/cover/6e390196-7c19-4a64-88db-69745dd95ccd/329746-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] Malware CreationCourse Thumbnail](https://cdn.inflearn.com/public/courses/329633/cover/9a4806ae-b981-4509-9209-923b1e405631/329633-eng.png?w=420)
![[Eduwill White Hacker Training Course] Embedded HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329609/cover/891f6ed4-f069-42d4-ad03-f9be3fb13a29/329609-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] Network TheoryCourse Thumbnail](https://cdn.inflearn.com/public/courses/329569/cover/0379ff30-dec1-4464-a752-ecb403e33f1f/329569-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] APT Malware CreationCourse Thumbnail](https://cdn.inflearn.com/public/courses/329345/cover/8862aa77-d04d-402d-bbb9-ec626702e629/329345-eng-original.jpg?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 1 Practical Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329281/cover/39775848-70b1-40a9-93ab-bfc0f3fe0d66/329281-eng.png?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 1 Written Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329280/cover/3022bf0b-85d4-4fa9-9b82-746ba0926bc4/8.jpg?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 2 Practical Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329279/cover/acfb1be4-0aa8-40cb-9bf7-1c7924ff89f1/329279-eng.png?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 2 Written Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329250/cover/73bf39ad-abc4-4e3a-a901-519f04246b6c/329250-eng.png?w=420)