✅ Malware creation
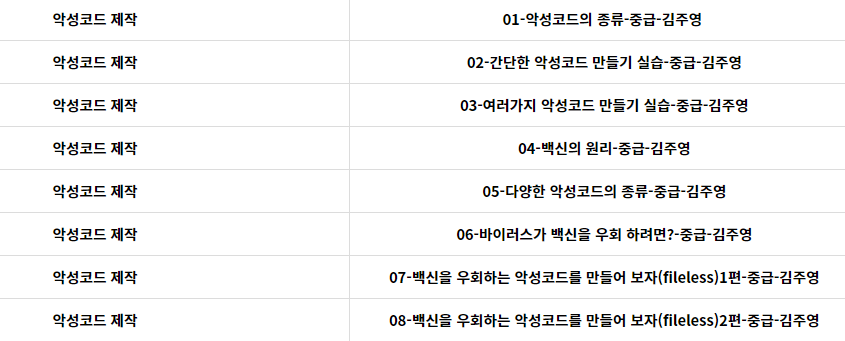
Malicious code (Malware) is a general term for any code that is not designed for "normal" functions, but rather for "malicious" purposes that harm users. The Information and Communications Network Act defines it as a "malicious program." Its implementation methods include computer viruses, Trojan horses, and worms, and it is sometimes given a separate name based on its actual behavior.
These days, unlike in the past, malware distribution increasingly utilizes multiple means to evade security procedures, and the reason for malware distribution is increasingly shifting toward the realistic(?) goal of "making money." Therefore, it is difficult to classify malware by just the three major implementation methods used in the past. Furthermore, very unique cases, such as ransomware, have emerged, so the distinction based on implementation method is almost disappearing these days. Even security experts often use the terms interchangeably, or even misuse them.
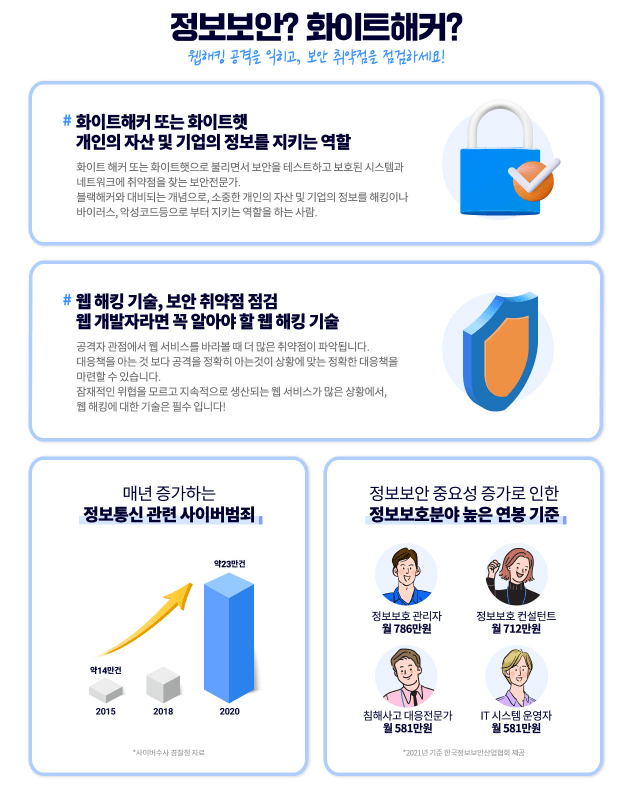
In fact, it's safe to say that Korea is the only country that truly calls malware by its proper name, having established the term "malware" as a government policy from the outset. This has led to criticism in the security industry for its use of vulgar terms. There are even instances of governments developing malware for cyberwarfare purposes, targeting key institutions and facilities in opposing countries.
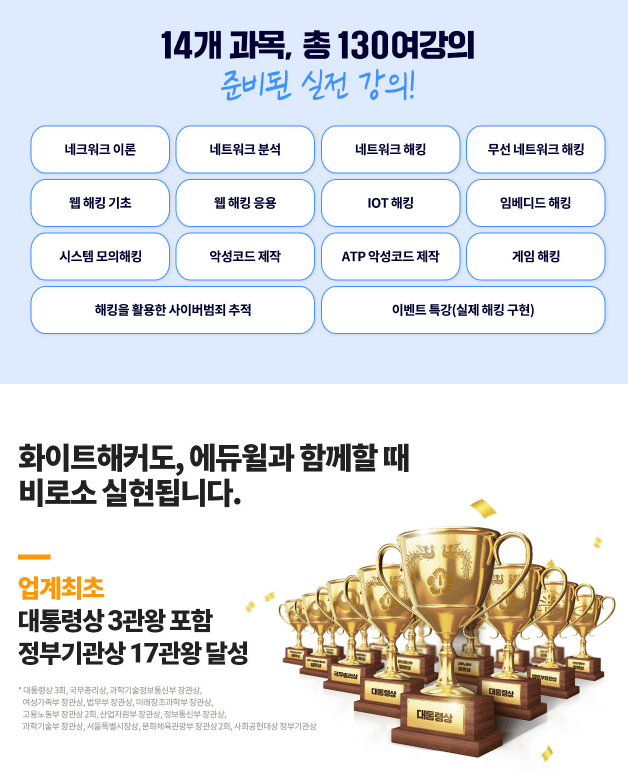
Let's learn the principles of malware creation, antivirus software configuration, and how to bypass them :)
Q. Can non-majors follow along?
Yes, of course you can. However, there are some prerequisite knowledge required for learning, so be sure to check the [Prerequisite Knowledge] section below!
![[Eduwill White Hacker] Tracking Cybercrimes Using Hacking (OSINT)Course Thumbnail](https://cdn.inflearn.com/public/courses/330474/cover/dcce6b36-ed1b-48f0-a42b-3cd4fa477dc0/330474-eng.png?w=420)








![[Eduwill White Hacker Training Course] Web Hacking Techniques (Basic + Application)Course Thumbnail](https://cdn.inflearn.com/public/courses/330444/cover/f1e3c27c-1528-41b7-b307-ac27a997c1c8/330444-eng.png?w=420)
![[Eduwill White Hacker] Game HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329746/cover/6e390196-7c19-4a64-88db-69745dd95ccd/329746-eng-original.png?w=420)
![[Eduwill White Hacker] Network AnalysisCourse Thumbnail](https://cdn.inflearn.com/public/courses/329693/cover/4a4b65e9-9621-4884-815b-efbdd604c685/329693-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] System Simulation HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329610/cover/22f513f5-3a82-4c72-8d0e-b6b4d3031d93/329610-eng.jpg?w=420)
![[Eduwill White Hacker Training Course] Embedded HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329609/cover/891f6ed4-f069-42d4-ad03-f9be3fb13a29/329609-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] Network HackingCourse Thumbnail](https://cdn.inflearn.com/public/courses/329607/cover/a65f460e-d036-42c4-be08-bec2a4947910/329607-original.png?w=420)
![[Eduwill White Hacker Training Course] Network TheoryCourse Thumbnail](https://cdn.inflearn.com/public/courses/329569/cover/0379ff30-dec1-4464-a752-ecb403e33f1f/329569-eng-original.png?w=420)
![[Eduwill White Hacker Training Course] APT Malware CreationCourse Thumbnail](https://cdn.inflearn.com/public/courses/329345/cover/8862aa77-d04d-402d-bbb9-ec626702e629/329345-eng-original.jpg?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 1 Practical Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329281/cover/39775848-70b1-40a9-93ab-bfc0f3fe0d66/329281-eng.png?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 1 Written Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329280/cover/3022bf0b-85d4-4fa9-9b82-746ba0926bc4/8.jpg?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 2 Practical Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329279/cover/acfb1be4-0aa8-40cb-9bf7-1c7924ff89f1/329279-eng.png?w=420)
![[Eduwill] 2022 Computer Utilization Ability Level 2 Written Short-Term PassCourse Thumbnail](https://cdn.inflearn.com/public/courses/329250/cover/73bf39ad-abc4-4e3a-a901-519f04246b6c/329250-eng.png?w=420)
