
Cloud Security Programming for Practical Use (AWS, Python, Terraform)
rex
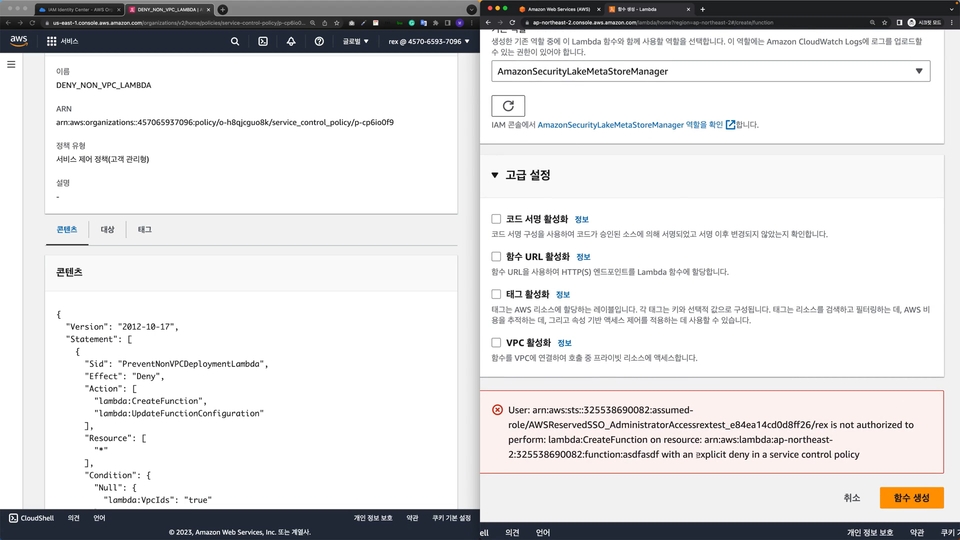
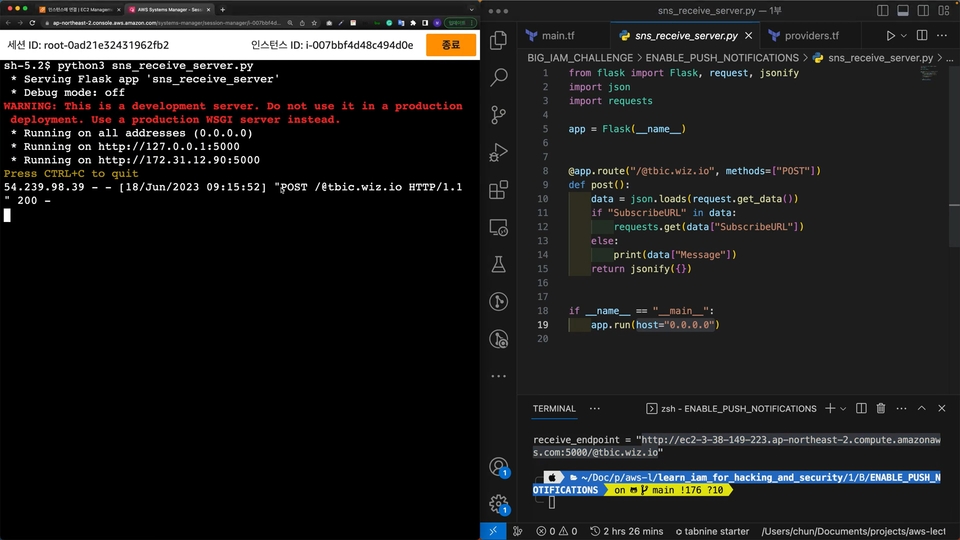
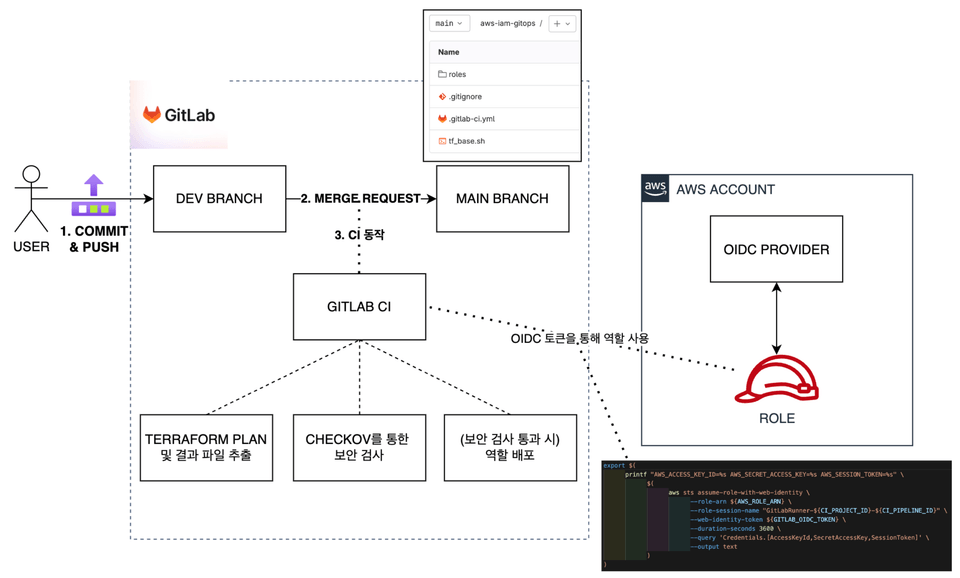
It is configured to allow you to learn programming languages (Python, Terraform) for the cloud. You can directly create and apply simple yet tedious repetitive tasks, track when and how you deployed, and implement your company's unique policies that specific solutions cannot address. Specifically, we will apply a security architecture using Terraform, the most popular IaC (Infrastructure as Code) application, and also proceed with creating an ultra-simple dashboard using Python!
초급
Python, Terraform, AWS








![[DevOps] Creating a fast and secure application deployment pipeline (CI/CD)강의 썸네일](https://cdn.inflearn.com/public/courses/332182/cover/f1183942-1754-4cc9-bd8f-8180146e5a1d/332182.png?w=420)











![[3-Week Completion] Cloud CS (AWS) for Senior-Level Advancement강의 썸네일](https://cdn.inflearn.com/public/files/courses/339607/cover/ai/0/04a386cd-9003-440b-a9a3-1a25ddfd63df.png?w=420)
