![[Eduwill White Hacker] Network Analysis강의 썸네일](https://cdn.inflearn.com/public/courses/329693/cover/4a4b65e9-9621-4884-815b-efbdd604c685/329693-eng-original.png?w=420)
[Eduwill White Hacker] Network Analysis
eduwill
Learn the skills to analyze vulnerabilities and defend against hacking through network analysis!
중급이상
Wireshark
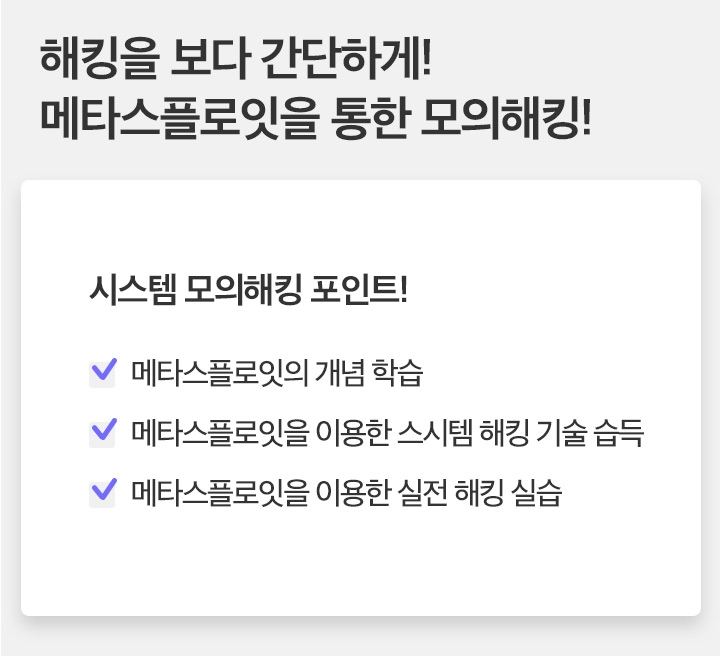
Metasploit Definition A tool that allows you to use known vulnerability attacks with CVE numbering, a mock hacking test tool that helps make hacking easier.

Linux
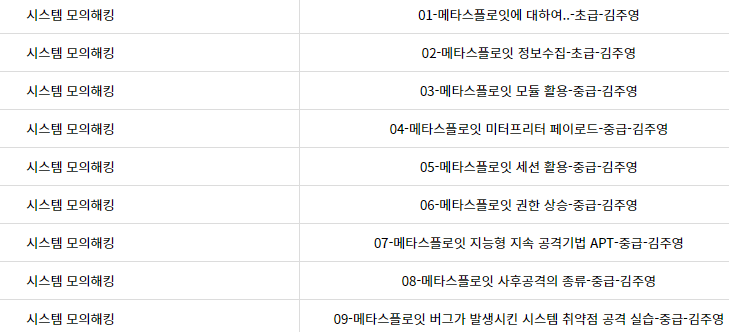
Simulated hacking using metasploit

📢 Please check before taking the class.
Introducing the subjects of the 'White Hacker' course :)
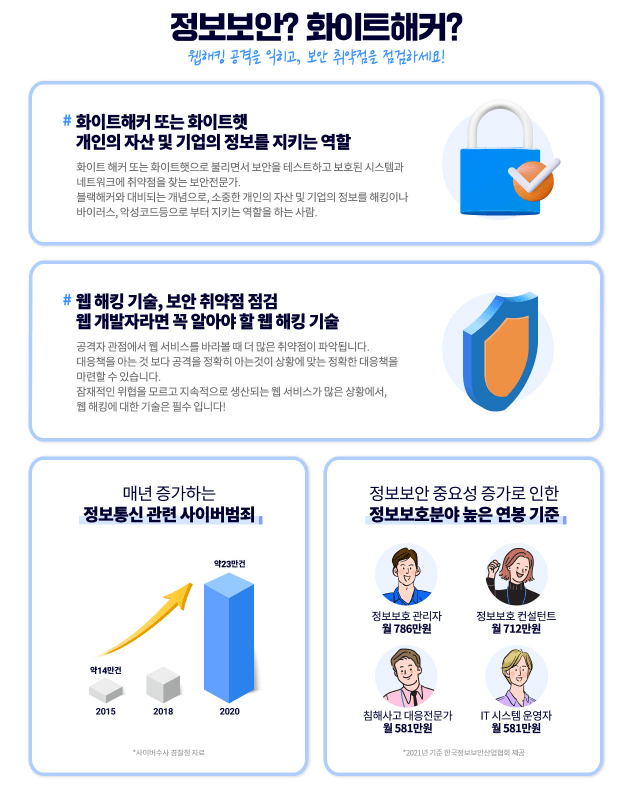
It is used as a term similar to a mock hacking test , and simulates actual attacker behavior (=hacking) as part of a process to actively evaluate an organization's information security level .
Commonly exploited security vulnerabilities and how to identify vulnerabilities using various techniques.
Typically, penetration testing (simulated hacking) is a method to check IT security and devise a response strategy against hacking through testing.
This is a performance test conducted after receiving prior approval from the security manager for the customer system.
Client networks, servers, web applications, mobile platforms, wireless systems, printers, modems, etc.
Test network environments that could be exploited for cybercrime .
📢 Please check the precautions!
Q. Can non-majors follow along?
Yes, of course you can. However, there are some prerequisite knowledge required for learning, so be sure to check the [Prerequisite Knowledge] section below!

Learn IT with Eduwill! 🎓

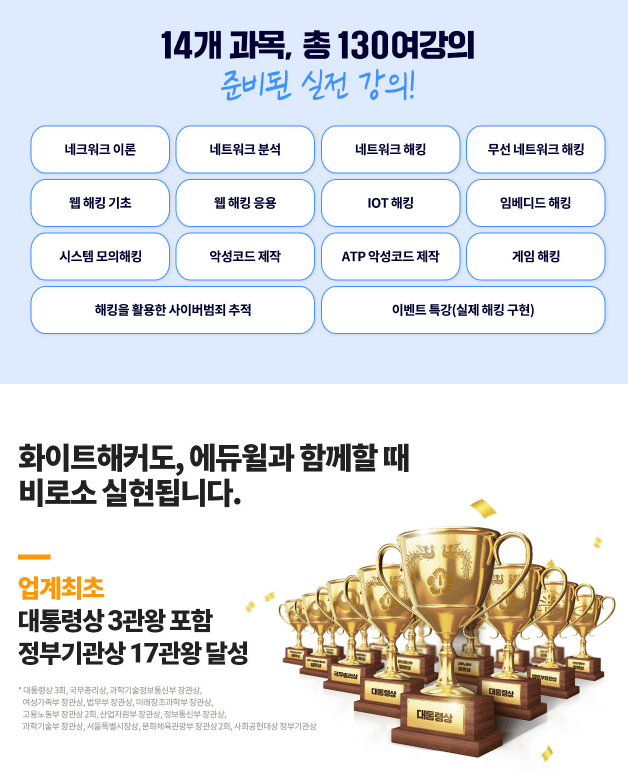
Who is this course right for?
Essential mock hacking for information security
Simulated hacking via web+Metasploit
Need to know before starting?
Linux
C language
All
11 lectures ∙ (8hr 34min)
All
3 reviews
5.0
3 reviews
Reviews 4
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
Reviews 10
∙
Average Rating 5.0
Limited time deal
$69,300.00
30%
$77.00
Check out other courses by the instructor!
Explore other courses in the same field!