
Notion Essentials
jejucoding
Say goodbye to complicated collaboration tools! 👋 From Markdown to databases, the essential skills of a workaholic can be done with Notion 🚀
입문
Notion, Team Collaboration Tool
Are you curious about how hacking attacks are carried out? Are you curious about how to defend? Let's perform a brute force attack using simple python code. Through this, you will learn how attacks and defenses are carried out. :)
Hacking attack
Information Security
brute force attack
Brute Force Attack


The order doesn't matter. You can start with Information Security Pathfinder, or you can start with this lecture.
[Click on the image to go to the lecture.]

[This text is for search engine optimization.]
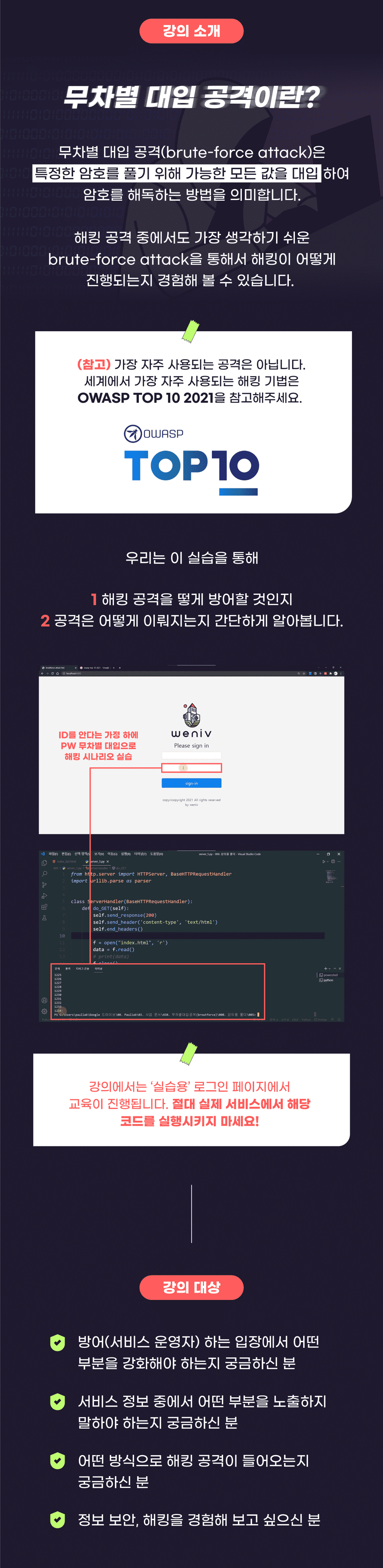
※ Caution: If you launch this attack on an actual service, it is a crime.
All legal responsibility lies with the party who hacked.
So never run that code on a real service.
Studying hacking and information security
What should I do,
What should I do first?
Have you ever wondered if it suits your aptitude?
Or from the standpoint of defense (service operator)
Which areas need to be strengthened,
Which parts should not be exposed,
Are you curious about how attacks come in?
Or are you just here out of curiosity?
So I prepared it.
Just try it once.
You don't necessarily have to type the code together.
Check what knowledge you lack,
Take a look at what you should study next.
Or enhance the security of your service.
✅ What is a brute force attack?
: A brute-force attack is
It means trying all possible values to solve a specific password. Wiki
Among the hacking attacks, the easiest to think of is through
The course is structured to give you an experience of how hacking is done.
(It is not the most frequently used attack. The most frequently used hacking technique in the world is
Please refer to OWASP TOP 10 2021. )
How do we defend against this attack?
Let's take a quick look at how the attack works.
Then I'll see you in class.
This lecture is a continuation of the Information Security Pathfinder lecture.
The order doesn't matter. You can start with Information Security Pathfinder, or you can start with this lecture.
Who is this course right for?
Anyone who was curious about how hacking attacks are carried out
For those of you who have ever wondered how brute force attacks work
Those considering a career in information security
Need to know before starting?
python
104,437
Learners
2,691
Reviews
163
Answers
4.8
Rating
80
Courses

제주에서 가장 핫한 개발자들이 모여 작당한 부트캠프! 열정있는 청년들에게 열정만큼 성장할 수 있는 기회를 제공합니다!
제주코딩베이스캠프는 제주에서 가장 큰 ICT 교육 행사로 카카오, 구름, 제주산학융합원 등 기업 지자체와 함께 진행하고 있습니다.
서비스 구축 성공 경험을 통해 이 취업난 시대에 자신감, 자존감, 성취감, 그리고 자립할 수 있는 능력을 배양해 보세요!
으라차차 청춘 화이팅입니다! 😀

All
22 lectures ∙ (2hr 31min)
Course Materials:
6. Create a password
04:04
All
36 reviews
4.9
36 reviews
Reviews 3
∙
Average Rating 5.0
Reviews 3
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
Reviews 6
∙
Average Rating 4.8
Reviews 1
∙
Average Rating 5.0
Free
Check out other courses by the instructor!
Explore other courses in the same field!