
Hacking as a hobby #2 (hacker's computing)
caliber50
You now have more freedom in cyberspace than ever before.
입문
Penetration Testing
Covering the content of WebGoat, the classic wargame of web hacking, we have translated and solved all the lessons and challenges from beginning to end. We provide all the tools and data needed to solve the challenges, starting with setting up the practice environment.
606 learners
Level Basic
Course period Unlimited

Reviews from Early Learners
5.0
김진호
Honestly, this is Hyeja. There is a place that offers a 5-day lecture through Webgoo, but they charge 150,000 won per person without even finishing the course. ㅂㄷㅂㄷ...
5.0
이지혁
Honestly, I thought I would be satisfied with just learning SQL injection, but there were many unexpected contents, and they were explained kindly, so I was able to learn easily even though there was a lot of content. It doesn't just pick out the easy parts, but really includes all the contents. It even solves problems with real bugs...
5.0
문대현
It's fun Easy and well explained!
Ability and acumen to discover web application vulnerabilities based on OWASP Top 10.
Computer science knowledge relevant to each challenge.
Hacking as a hobby, hacking as a hobby.
※ "Hacking as a Hobby" content only focuses on legal hacking to contribute to a safe information security ecosystem.

< To view the course content in book form: Paper book/e-book (link) >
Here, we'll master WebGoat, a classic web hacking wargame . Based on fully translated Korean materials, we'll follow every lesson from start to finish and practice the challenges.
They will be exposed to the hidden parts of the web browser. They will intercept and modify data transmissions, requesting special information from servers. They will even access private pages that are inaccessible to the general public. They will extract personal information stored in databases as if it were a given . They will even use websites to deceive other users .
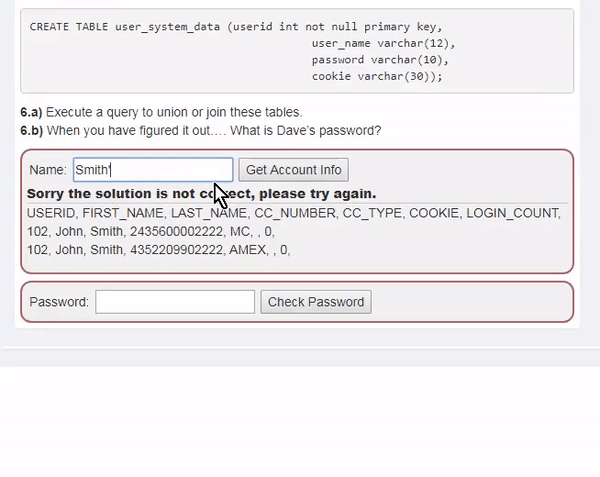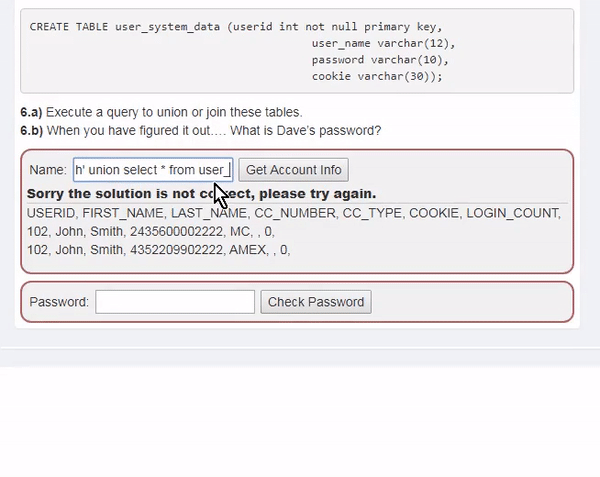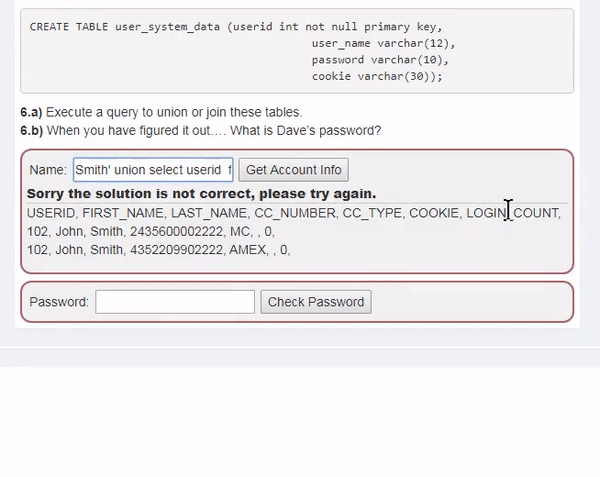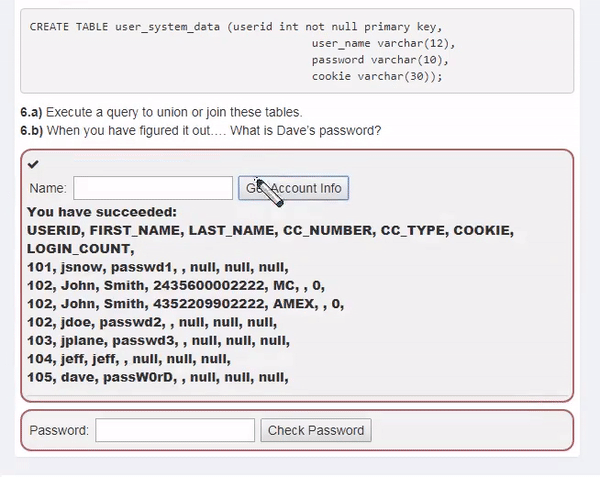
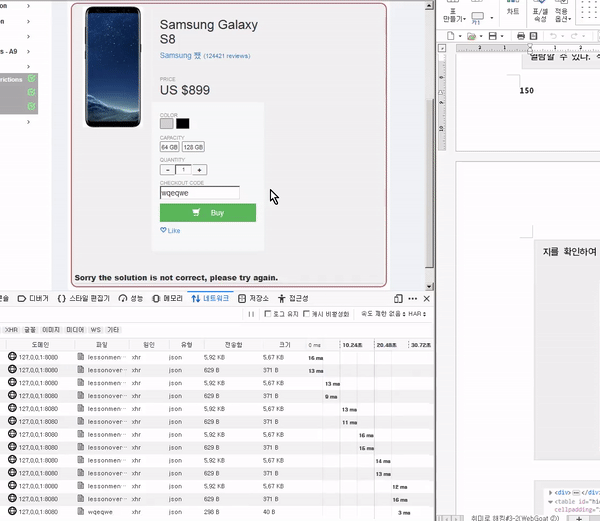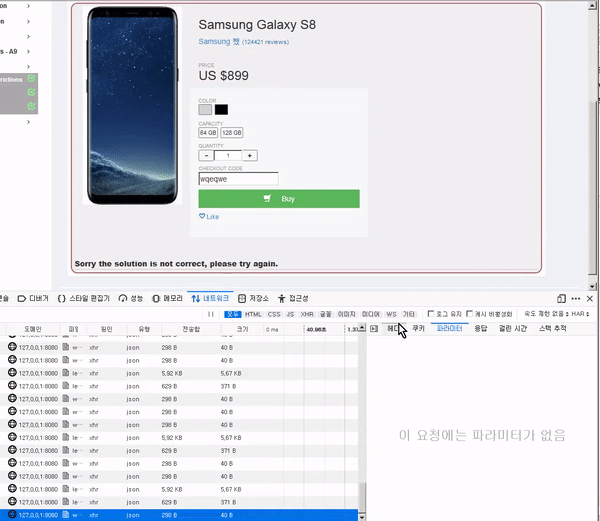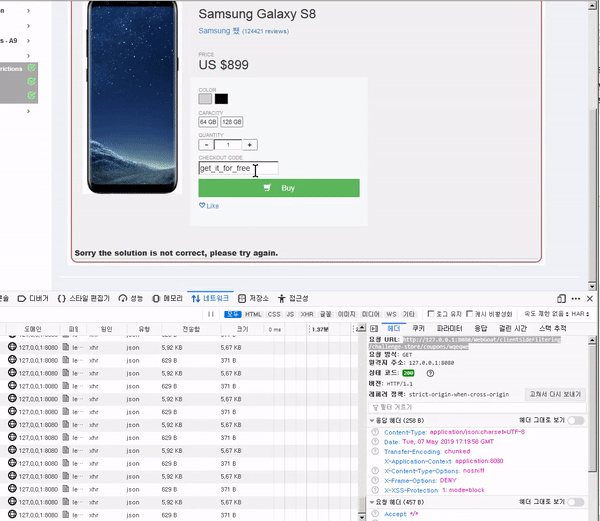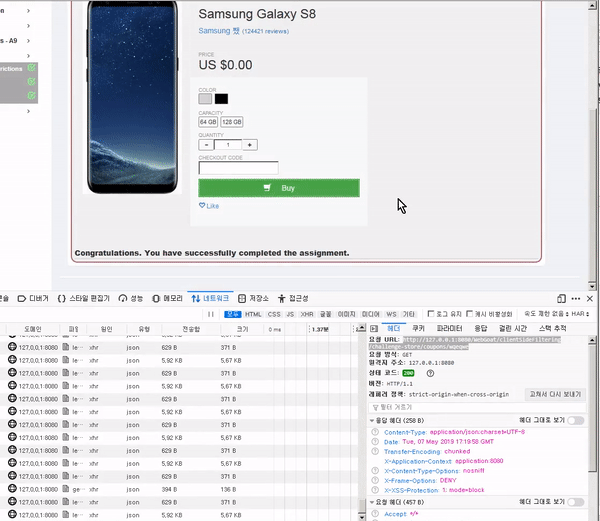
This course will teach you how to discover and mitigate various web-related security vulnerabilities . Specifically, it covers theory and practice on vulnerabilities related to SQLI, XXE, authentication bypass, JWT, XSS, IDOR, access control, deserialization, CSRF, vulnerable components, password reset, and HTML tampering.
To reduce any additional hassle, we'll help you set up a practice environment and provide all the tools and data you need to solve the challenge.
 |  |
 | |
[Q1] Which version of Webgoat do you use?
[Ans] We use M24 version with OWASP 2017 applied.
[Q2] I didn't take "Hacking as a Hobby #1-2." Is it okay to start with this course?
[Ans] Yes, that's not a problem. Course #2 focuses on general hacking experience, while course #1 focuses on system hacking. However, course #3 focuses on web hacking, so it's not directly related. However, course #5, which covers actual hacking competitions, covers a broader range of topics, including systems and the web, so the previous courses are not meaningless.
[Q3] What abilities will you gain when you complete the course?
[Ans] A website developed by a novice developer unfamiliar with security may seem like a toy. However, please note that this isn't the entirety of web hacking. It's about demonstrating a few skills based on key vulnerabilities . Now, you're finally ready to take action.
Who is this course right for?
For those who want to complete all the content of Wargame WebGoat.
Anyone who wants to learn hacking little by little as an academic hobby.
Anyone who wants to participate in domestic/international hacking competitions in the future.
Students in related departments who need to supplement their major knowledge.
Those who wish to pursue a career in information security.
Need to know before starting?
If you have experience writing Java programs, it may be helpful.
11,801
Learners
1,005
Reviews
118
Answers
4.7
Rating
9
Courses
ㆍ Information Security Engineer
ㆍ Author of "Coding Everybody! Python"
ㆍ Author of "Hacking as a Hobby #N" (Book & Lectures)
ㆍ Information Security Officer at Hankuk University of Foreign Studies
ㆍ CERT Team Leader at Missile Strategy Command (Army OCS #59)
ㆍ B.S. in Computer Science and Engineering, Tech University of Korea (4.42 GPA)
All
62 lectures ∙ (10hr 2min)
1. 1. Prologue
03:01
5. 5. General(1)
07:46
6. 6. General(2)
07:33
7. 7. General(3)
10:27
18. 18. XXE(1)
10:32
19. 19. XXE(2)
10:02
20. 20. XXE(3)
12:56
21. 21. XXE(4)
12:38
22. 22. XXE(5)
06:11
All
25 reviews
4.6
25 reviews
Reviews 1
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
5
Honestly, I thought I would be satisfied with just learning SQL injection, but there were many unexpected contents, and they were explained kindly, so I was able to learn easily even though there was a lot of content. It doesn't just pick out the easy parts, but really includes all the contents. It even solves problems with real bugs...
Reviews 9
∙
Average Rating 4.9
Reviews 87
∙
Average Rating 4.5
Reviews 4
∙
Average Rating 5.0
$42.90
Check out other courses by the instructor!
Explore other courses in the same field!