
웹 개발자와 정보보안 입문자가 꼭 알아야 할 웹 해킹 & 시큐어 코딩
크리핵티브
정보보안 입문자와 웹 개발자 분들을 위한 웹 해킹 입문 강의! 본 강의를 시작으로 웹 해킹을 재미있게 시작해보세요!
초급
모의해킹, 인젝션
The ultimate web hacking master! File upload vulnerability attack technique! This is a training that will further improve the students' web hacking skills through a completely different approach from the existing known methods!

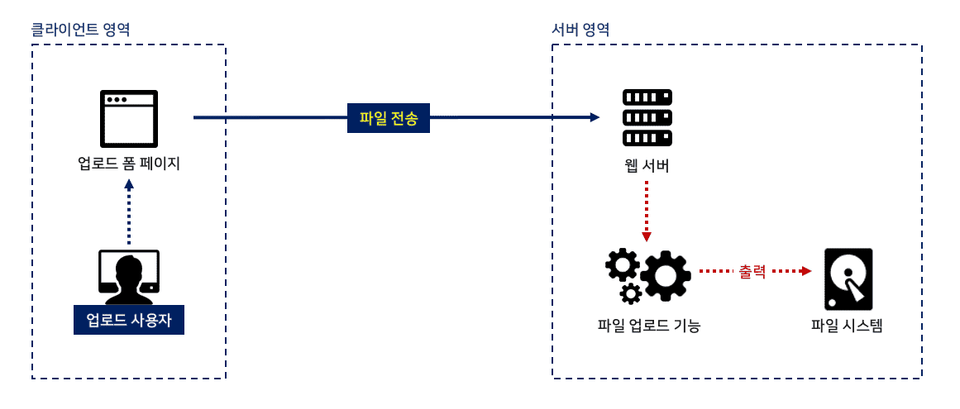
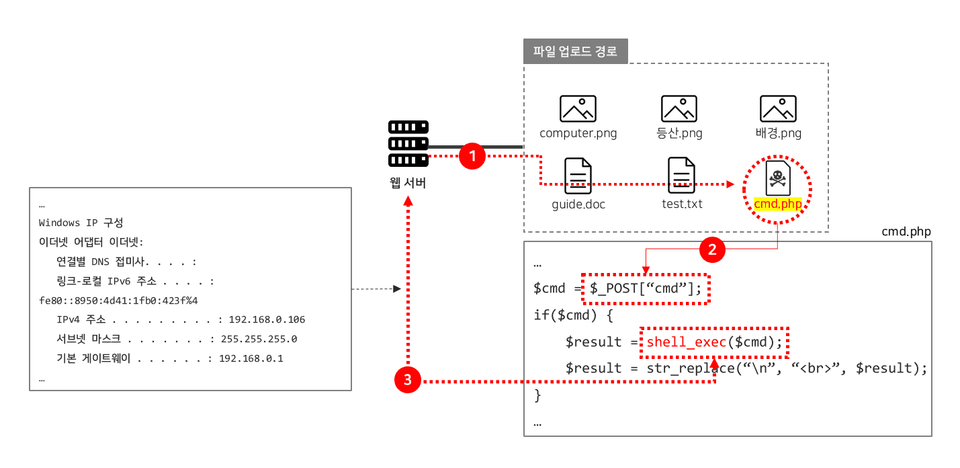
How the file upload function works
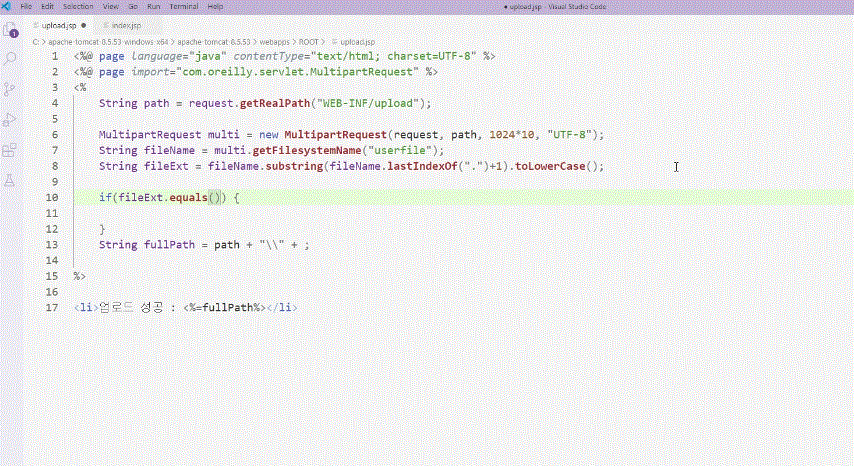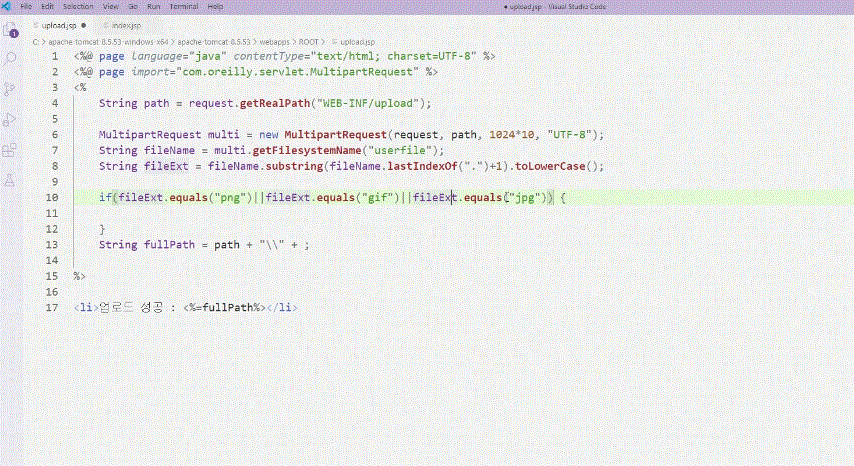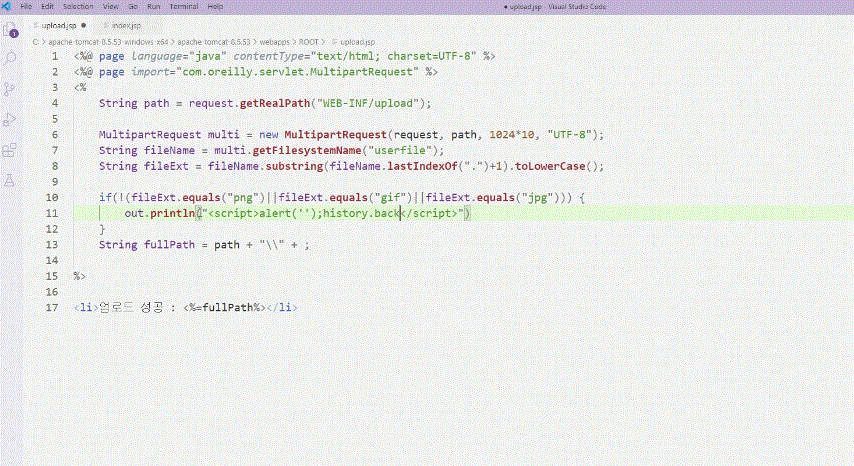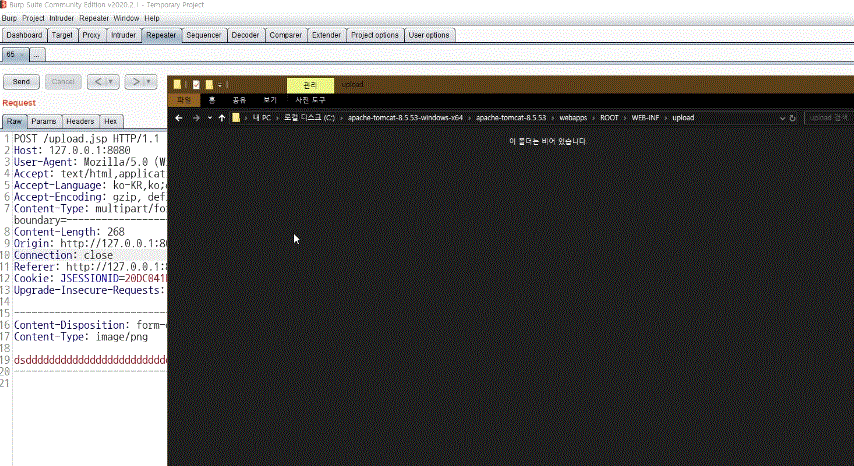
File upload vulnerability principle
Understanding web shells and how they work
File upload vulnerability attack methodology
File Upload Vulnerability Secure Coding Techniques
Practical attack techniques
File upload vulnerabilities are an attack technique that utilizes a malicious script called a WebShell to take control of a server. The attack doesn't stop at a single server, but can extend into the internal network . This is truly a devastating attack!
File upload functionality is essential in today's web environment. Most of the websites we frequently use have file upload functionality! What if a web shell, a malicious script for attack, were uploaded through this feature?
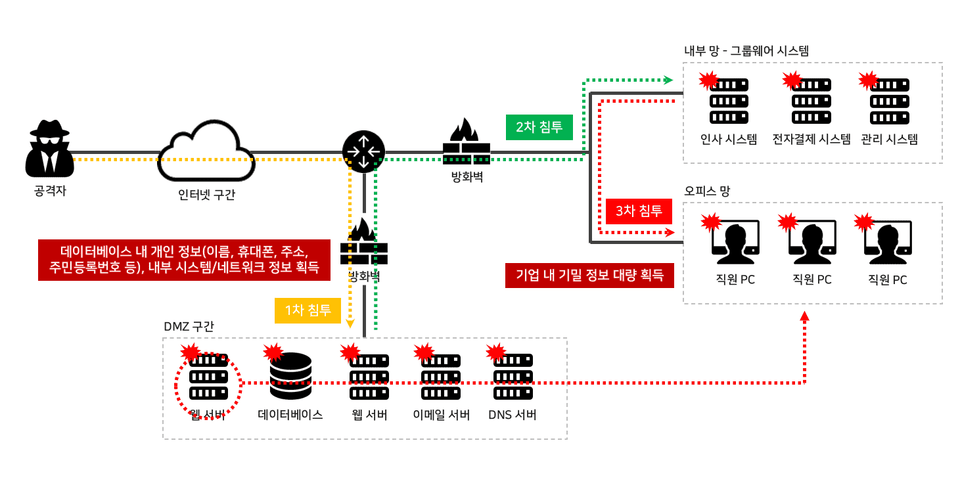
Numerous malicious hackers (black hackers) use this attack technique to penetrate internally via compromised web servers, deploying malware to employees, distributing ransomware, stealing confidential internal information, and stealing personal customer information. This is a truly terrifying attack!
Because of this influence, many companies cannot help but be sensitive to " file upload vulnerabilities ," and it is an attack technique that has even earned the title of " the ultimate boss " among practitioners!
If you are doing web hacking yourself or defending yourself, you now know what you need to know, right? ㅡ.,ㅡ;;
Those of you reading this right now likely fall into the following categories:
I would like to say it in one sentence.
This is the most persistent attack that digs into the field during diagnosis, and it is my personal favorite.
I would like to share with you the know-how I have gained over the years.
The training will be conducted from the basics, including the operating principles of the file upload function and the principles of file upload vulnerabilities.
We will go through each step in detail so that even beginners can easily understand.
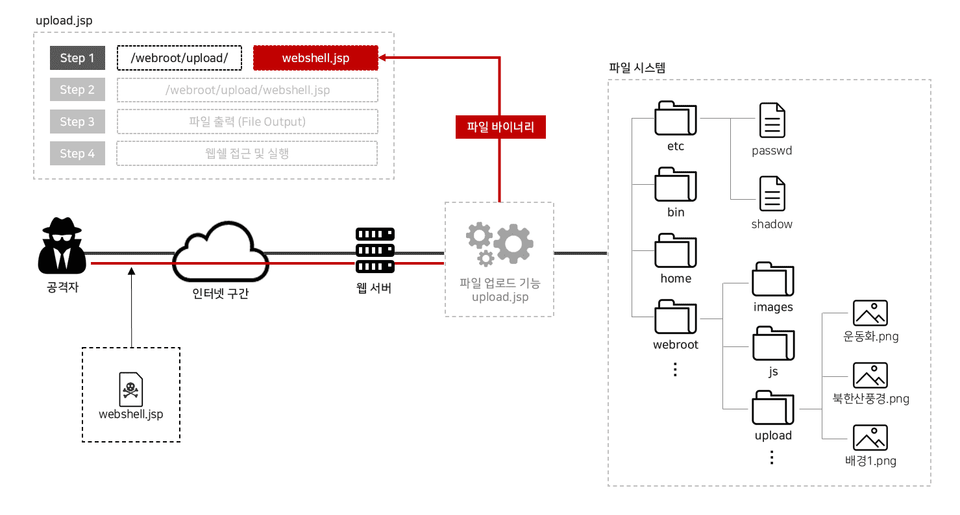
We'll cover the basic concepts, operating principles, and hands-on practice of creating a "web shell," a key element in file upload vulnerability attacks. Understanding web shells is essential!
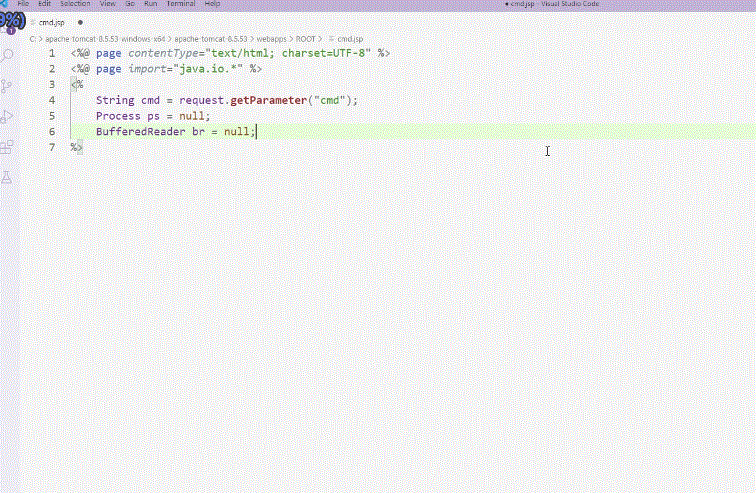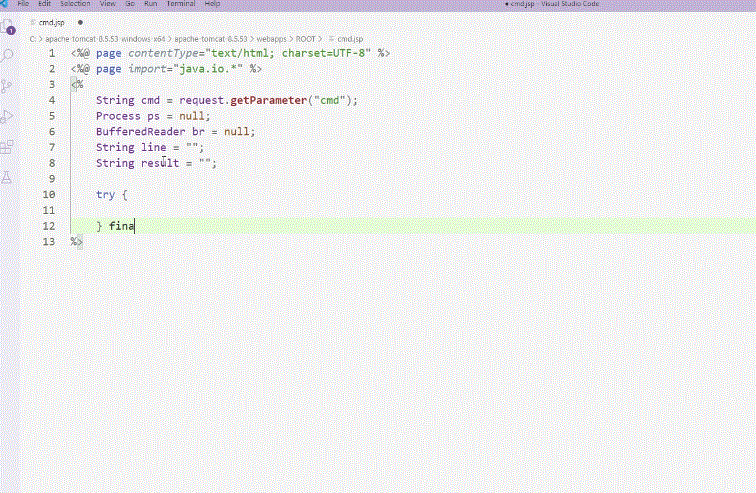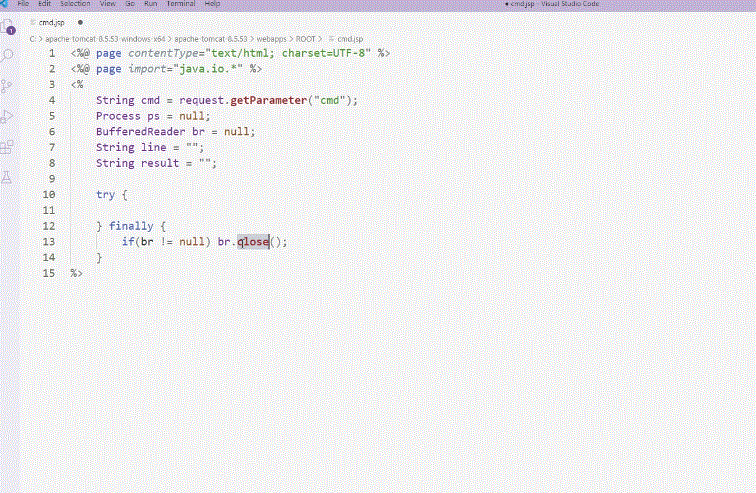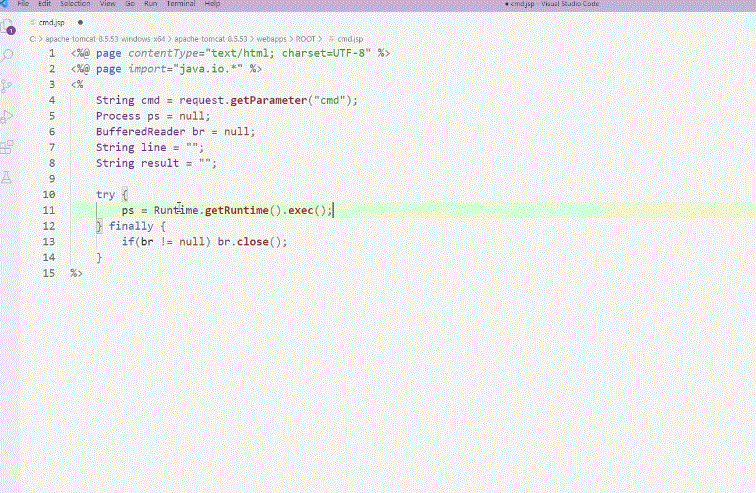
Expand your practical perspective with 12 case studies, and make the skills your own by practicing in the provided virtual environment!
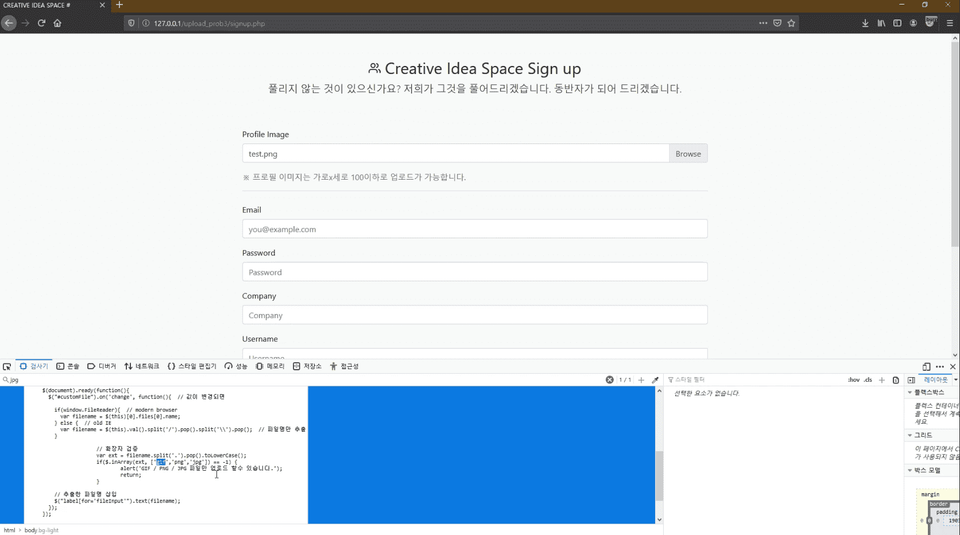
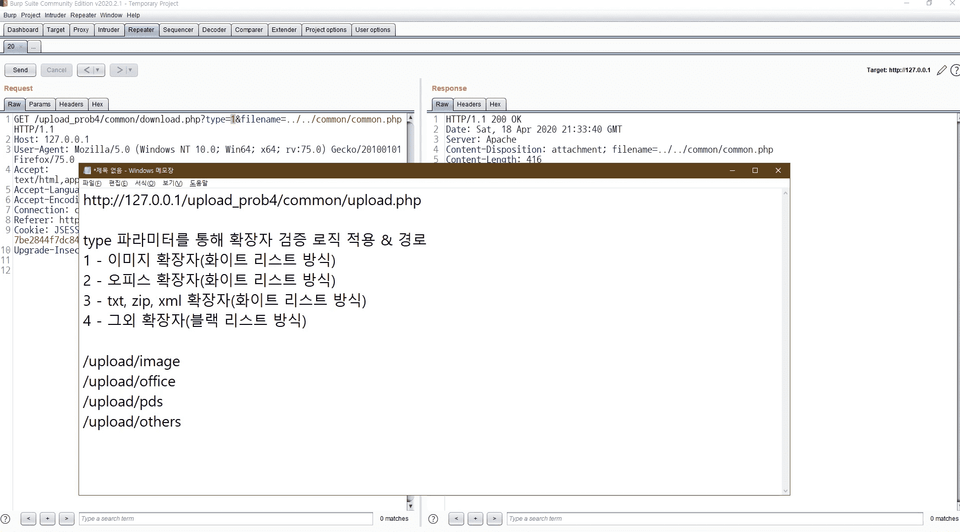
A total of 18 virtual practice environments are provided for JSP and PHP!
We often see diagnosticians being strong on offense but weak on defense. This stems from language barriers and a lack of understanding of secure coding. Practice can help you overcome these barriers!
※ How to use Burp Suite is not covered in this training. You can refer to the basic usage method in the training "Stories about Web Hacking and Simulated Hacking in the Field."
※ This training PPT uses Nanum font provided by Naver.
Who is this course right for?
For everyone from beginners to advanced web hackers.
hands-on worker
For those who want to know more about file upload vulnerability attack techniques
Need to know before starting?
Web Basics
Web Hacking Basics
26,082
Learners
1,381
Reviews
501
Answers
4.9
Rating
18
Courses
안녕하세요, 크리핵티브입니다.
다년간 다양한 웹 서비스를 진단하고 연구한 경험을 바탕으로, 실무에 바로 적용 가능한 지식을 인프런 플랫폼에서 공유해오고 있습니다.
그리고 웹 해킹 기초를 체계적으로 다룬 『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』을 집필했습니다. 기초가 부족한 분들께는 이 책으로 학습을 시작하실 것을 권합니다.
『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』 저자
이메일 : crehacktive3@naver.com
All
111 lectures ∙ (15hr 39min)
Course Materials:
All
67 reviews
Limited time deal
$66,000.00
25%
$68.20
Check out other courses by the instructor!
Explore other courses in the same field!