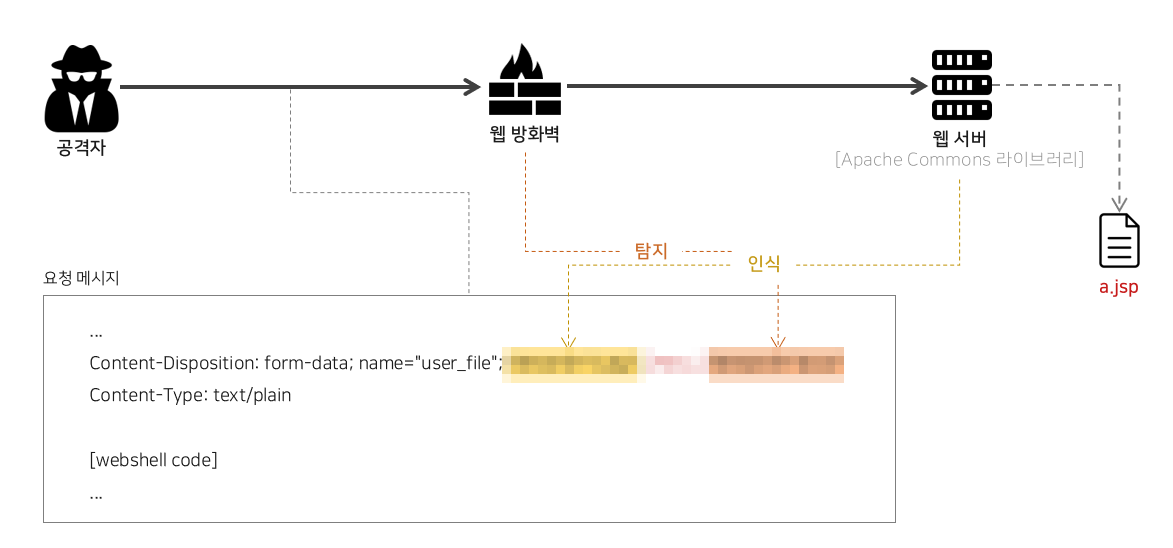
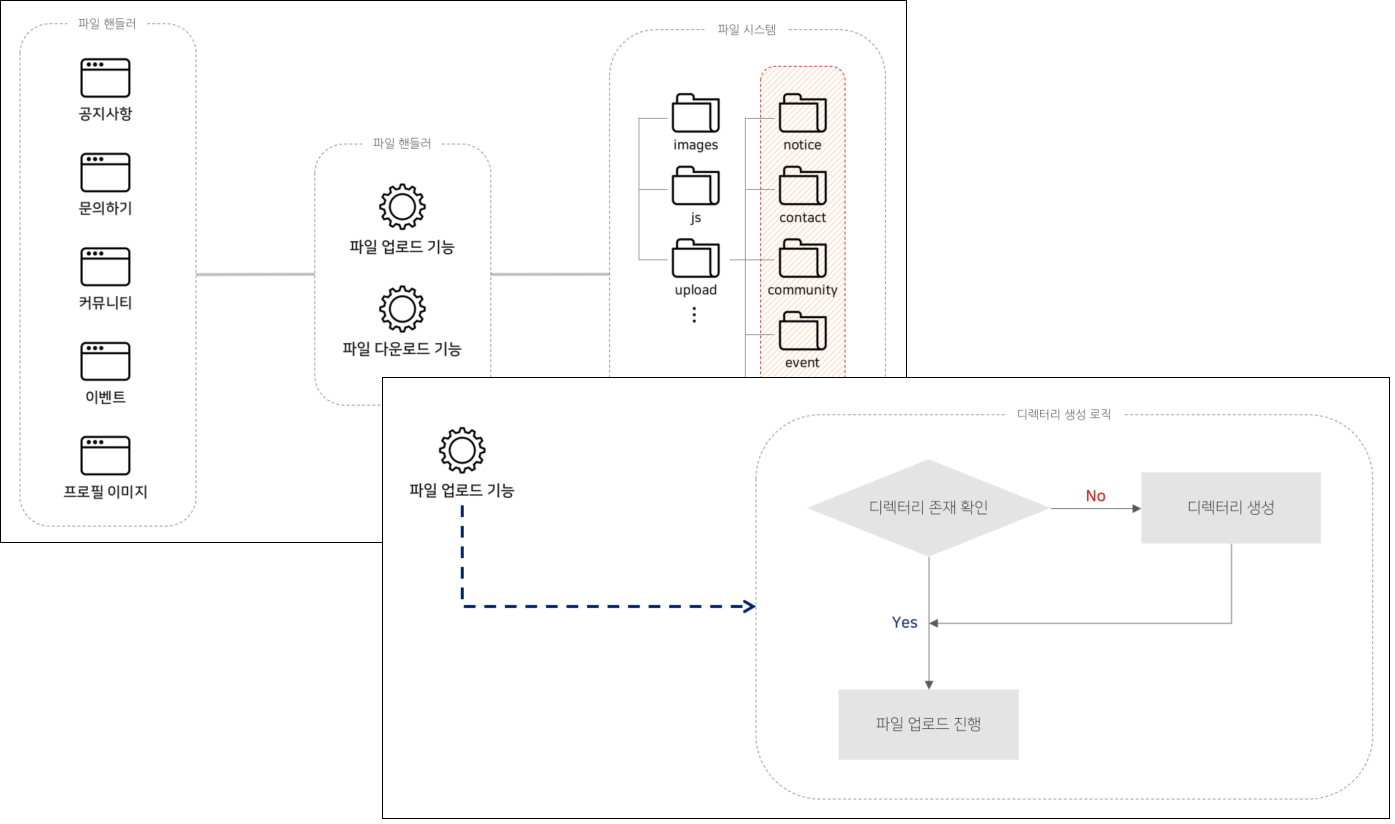
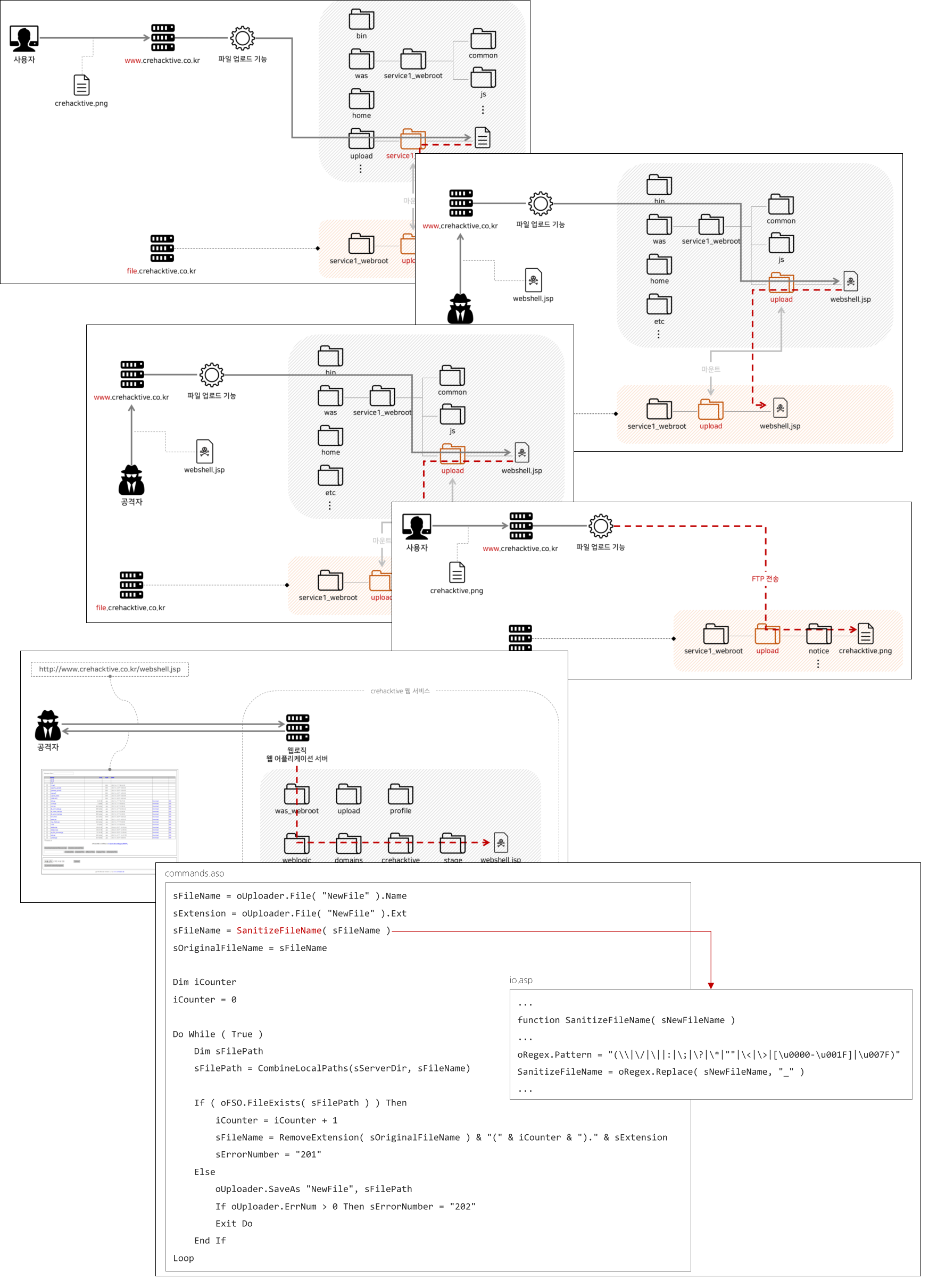
Web Hacking & Secure Coding That Web Developers and Information Security Beginners Must Know
crehacktive
$42.90
Basic / Penetration Testing, Injection
4.8
(246)
An introductory course on web hacking for information security beginners and web developers! Start web hacking in a fun way with this course!
Basic
Penetration Testing, Injection