
Web開発者と情報セキュリティの入門者が必ず知っておくべきWebハッキング&セキュアコーディング
crehacktive
情報セキュリティ入門者とWeb開発者のためのWebハッキング入門講義!今回の講義をはじめ、Webハッキングを楽しく始めましょう!
초급
Penetration Testing, Injection
SQL Injection, the flower of web hacking, explained by a mock hacking practitioner! Learn attack and defense at the same time.
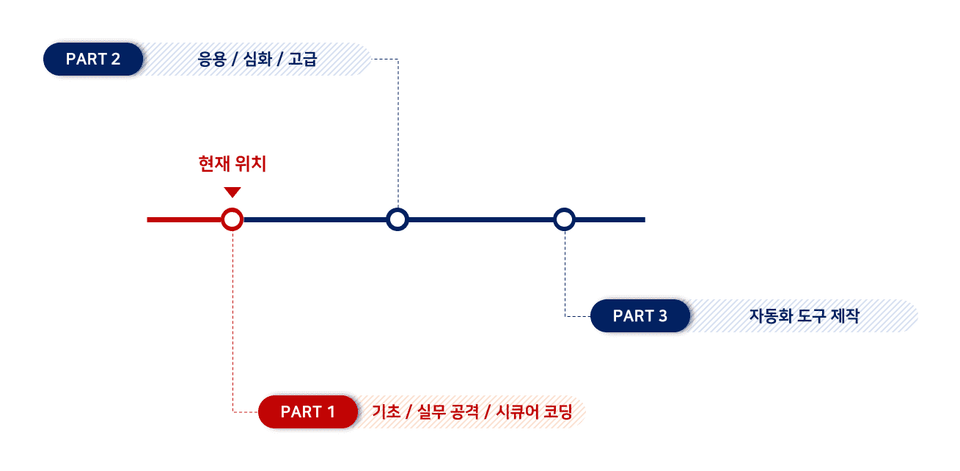
Building a basic understanding of vulnerabilities
Understand why vulnerabilities occur and the detailed principles
Identifying various attack points that occur in practice
Learn the attacks used in practice
Apply direct countermeasures to vulnerable functions and learn secure coding

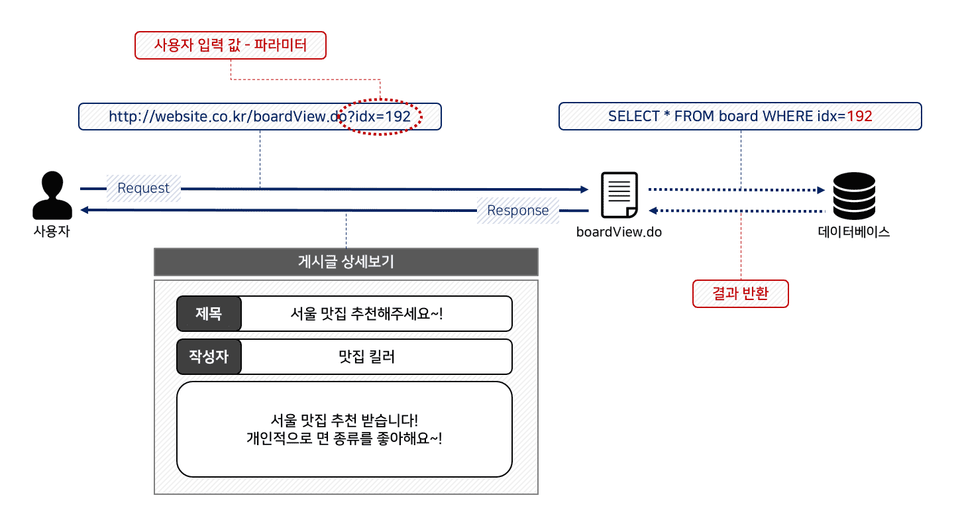
A popular figure in the web hacking world! The fact that so many people are aware of the attack means its impact is significant, right?
Most web applications today feature dynamic page generation based on user input. In this environment, attackers face a growing number of attack targets, necessitating effective analysis methods and adaptive attack techniques tailored to each situation. Conversely, defenders often implement inline security solutions or secure coding for effective defense. Understanding attacks is crucial for effective defense, right?
For effective vulnerability analysis, you'll learn how to analyze various attack points using specific methodologies. You'll also learn the appropriate attack techniques and the specific environments in which they should be used. This course covers each attack technique used in practice in detail.
We provide a practice bulletin board based on PHP-MYSQL, PHP-MSSQL, and PHP-ORACLE, through which you can practice SQL injection for various DBMS.
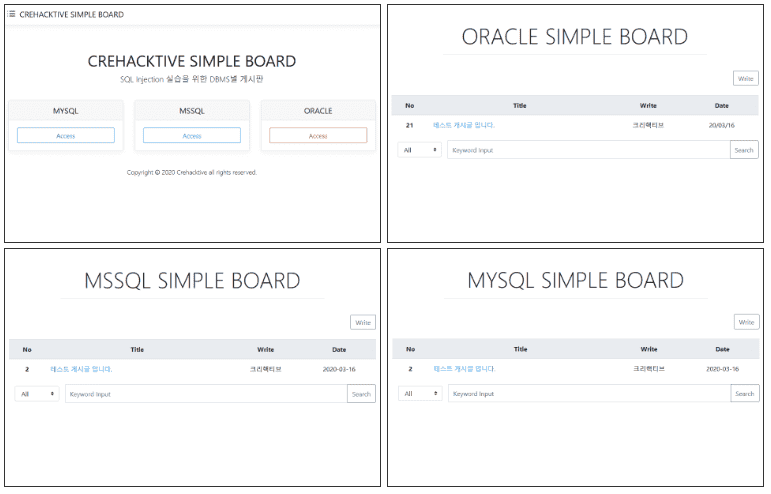
Each technical element for completing SQL Injection attack techniques does not end in theory.
We will conduct hands-on training for each DBMS.
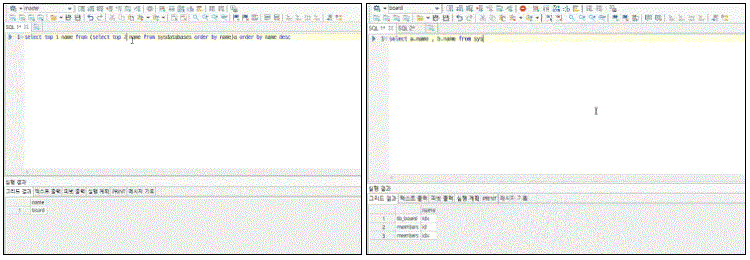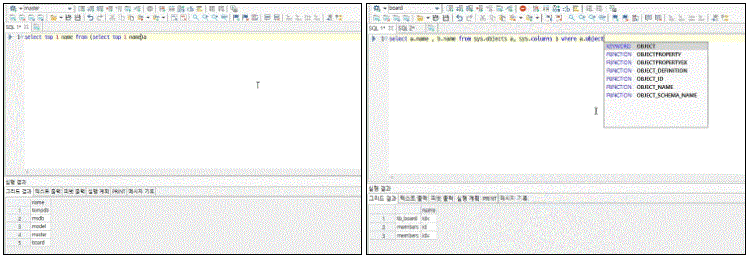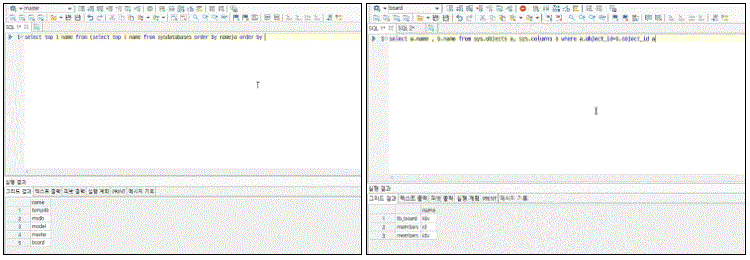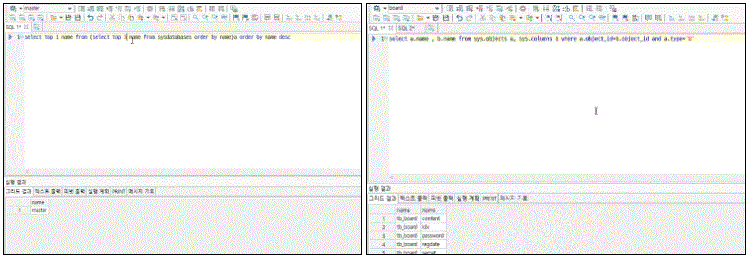
We'll take a closer look at the response measures for each function and conduct hands-on practice applying secure coding to vulnerable bulletin boards.
※ How to use Burp Suite is not covered in this training. You can refer to the basic usage method in the training " Stories about Web Hacking and Simulated Hacking in the Field ".
Q. I want to take the course, but is there anything I need to know beforehand?
A. Basically, you must know and listen to the basics of web and SQL grammar , and it is also recommended to take additional web hacking training.
Q. If I complete the training, can I get a practical diagnosis?
A. Of course! However, simply receiving training isn't enough. To achieve satisfactory results, you need to study and practice on your own. To achieve anything, you need to put in the effort.
Q. Why is the training time so much longer than that of other mock hacking training programs for SQL injection?
A. This training is specialized and covers only SQL injection, so it's bound to be long. Of course, the approach will also be completely different. While existing attack approaches are separate and distinct, this training connects them into a single, unified framework. You'll also discover why you need to carry out this type of attack.
Q. Can non-majors and students also take the course?
A. Of course! However, you must complete the required viewing lectures below and fully understand them before taking this course.
※ This training PPT uses Nanum font provided by Naver.
Who is this course right for?
For those who want to learn SQL Injection properly
For practitioners who have difficulty finding SQL Injection vulnerabilities when diagnosing websites
For practitioners who only perform vulnerability diagnosis
People who can't attack without SQL Injection automation tool
For those who want to gather their knowledge about SQL Injection in one place.
If you want to know exactly what attack to do in what environment
For those who want to know the exact attack process
If you fail to provide the correct response plan
Need to know before starting?
Web Basics
Buff Suite Basic Usage
Web Hacking Basics
SQL Basic Grammar
26,167
Learners
1,387
Reviews
502
Answers
4.9
Rating
18
Courses
안녕하세요, 크리핵티브입니다.
다년간 다양한 웹 서비스를 진단하고 연구한 경험을 바탕으로, 실무에 바로 적용 가능한 지식을 인프런 플랫폼에서 공유해오고 있습니다.
그리고 웹 해킹 기초를 체계적으로 다룬 『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』을 집필했습니다. 기초가 부족한 분들께는 이 책으로 학습을 시작하실 것을 권합니다.
『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』 저자
이메일 : crehacktive3@naver.com
All
123 lectures ∙ (24hr 31min)
Course Materials:
All
108 reviews
4.8
108 reviews
Reviews 4
∙
Average Rating 5.0
Edited
5
I am currently working for an information security company, so I wanted to take related training, and I applied for and took this course. The result is very satisfactory. The instructor's expertise is evident throughout the lecture. The more I listened to the lecture, the more ashamed I felt of myself for having only done superficial diagnoses. I didn't know what kind of attacks to perform in what kind of environment, but through this training, I was able to clearly understand what attacks to perform depending on the environment. Also, it seems that the instructor created the attack process himself, and I think it will be really helpful in practical diagnosis. There are many times when I have to attack, but I just stare blankly at the parameters and don't know what to do, but if I refer to this, I think I can smoothly perform the diagnosis sequentially. Oh, and that roadmap is amazing. I printed it out. I've only watched it once now, but I'm going to watch it two more times as the instructor said. Thank you, instructor.
長受講評ありがとうございました!お役に立てたなんて本当に幸いですねㅎ大切な受講評ありがとうございます。良い一日をお過ごしください〜
Reviews 14
∙
Average Rating 4.5
5
原理一つ一つ説明してくださったので、隙のない知識を得たと感じました。プロセスを頭の中でずっと整理してみて診断をするようになったら何からしなければならないのかすぐに浮上するのがとても良かったです。現在ホワイトハッカーではないので、もう2度聞いて実習する環境をジャンゴ、スプリングを活用して作っているのですが、開発しながらもプロセスが思い浮かび、フィルタリングロジックを書きたいと思いました。次の講義であるPart 2,3,4も早く見たいですね! [計3回+@受講後追加] 初めて受講した時点で、セキュリティコンサルタントのキャリアを開始することになりました。そして何よりも、ペイロードをn年目の実務コンサルタントが理解できず、私に質問する様子を見ると、クリクリプティブ様の講義が多大な内空を持ったことに気づくことができました。繰り返し学習しながら、WAFバイパスや効率的なデータ照会などをすべて実務で活用できるようになりました。もう一度ありがとうございます。
プロセスが浮かび上がるなんて嬉しいですねㅎㅎ受講評を上手くくださりありがとうございます! 大切な受講評で力を得ますね。送ってください〜
Reviews 1
∙
Average Rating 5.0
Reviews 15
∙
Average Rating 5.0
Reviews 8
∙
Average Rating 4.9
$127.60
Check out other courses by the instructor!
Explore other courses in the same field!