Wireshark Network Packet Analysis Practice for IT Security
boanproject
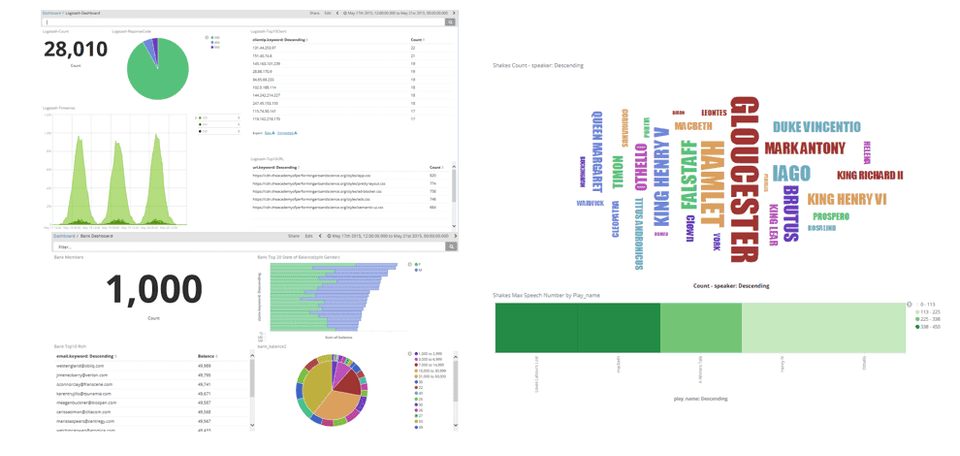
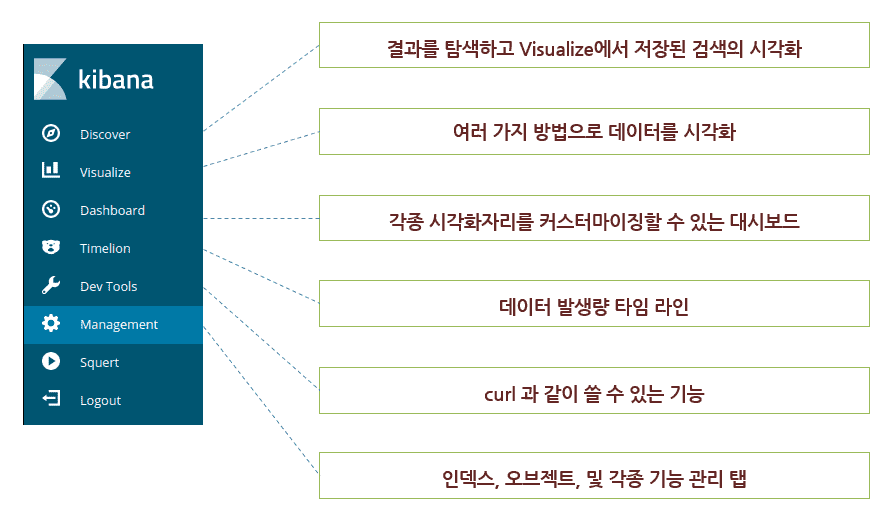
Network packet analysis is essential when conducting incident analysis and vulnerability analysis. Among the tools available, Wireshark is the most widely used, and this course covers the complete utilization of Wireshark and provides understanding through incident analysis case studies.
初級
Penetration Testing, Network, Wireshark