
웹 개발자와 정보보안 입문자가 꼭 알아야 할 웹 해킹 & 시큐어 코딩
크리핵티브
정보보안 입문자와 웹 개발자 분들을 위한 웹 해킹 입문 강의! 본 강의를 시작으로 웹 해킹을 재미있게 시작해보세요!
초급
모의해킹, 인젝션
The ultimate web hacking! File upload vulnerability attack technique! Part 2 of the 'Part 1' education follows Part 1 and covers more advanced techniques.

Understanding the Java File Upload Library
Potential security threat to Java file upload library
File upload vulnerabilities, advanced techniques!
We deliver the essential information that you won't find anywhere else.
This is a detailed training that covers the attack process of a completely different approach from the existing known methods, which is the most important content in file upload vulnerability attacks. You can learn the basic knowledge of attacks, bypass techniques used in practice, analysis of practice cases, various response measures, and secure coding. This is a mandatory training that serves as the basis for subsequent training.
This training course teaches advanced attack techniques and Web Application Firewall bypass techniques not covered in PART (1), and analyzes technical techniques used in practical environments through hands-on practice.
In today's web environment, web shell detection solutions are increasingly being used, and accordingly, diagnosticians must have the skills to bypass web shell detection solutions. Therefore, this will be essential training for practitioners.
The final part of our lecture on file upload vulnerabilities!
This lecture is the sequel to the lecture titled 'Part 2', 'File Upload Vulnerability Attack Techniques and Practical Case Analysis by a Simulated Hacking Practitioner: PART 1' .
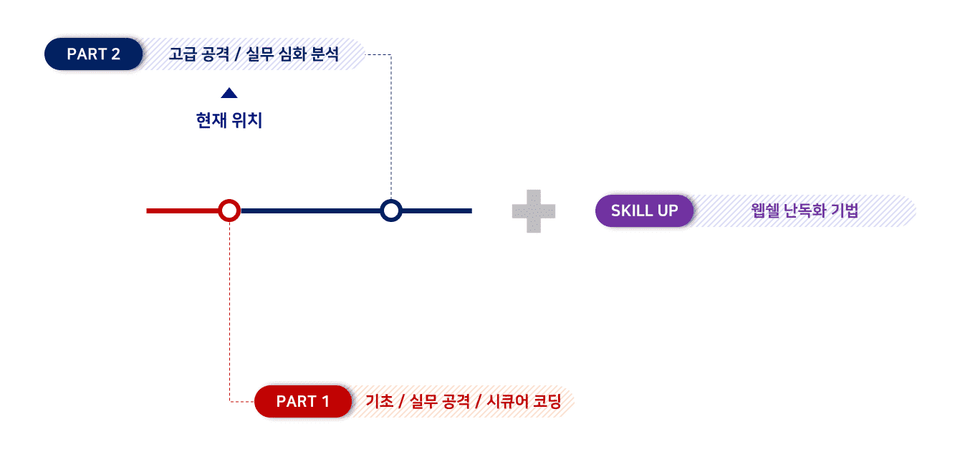
File Upload Vulnerability Attack Part 2 is divided into three parts , and each topic is as follows.
This lecture is Part 1 of Part 2, and covers the topic of 'File Upload Library Analysis and Attack Methodology' .
I'm listening to the Creative Web Hacking series.
There are many ways to learn web hacking today. Most of the common ones, such as online lecture platforms like Inflearn, offline lectures at academies, and search engines, tend to focus on general content.
But this lecture is different. We are proud to say that it is 'content you can't hear anywhere else!'
💡 This lecture is Part 1 of Part 2 , and covers 'File Upload Library Analysis and Attack Methodology' .
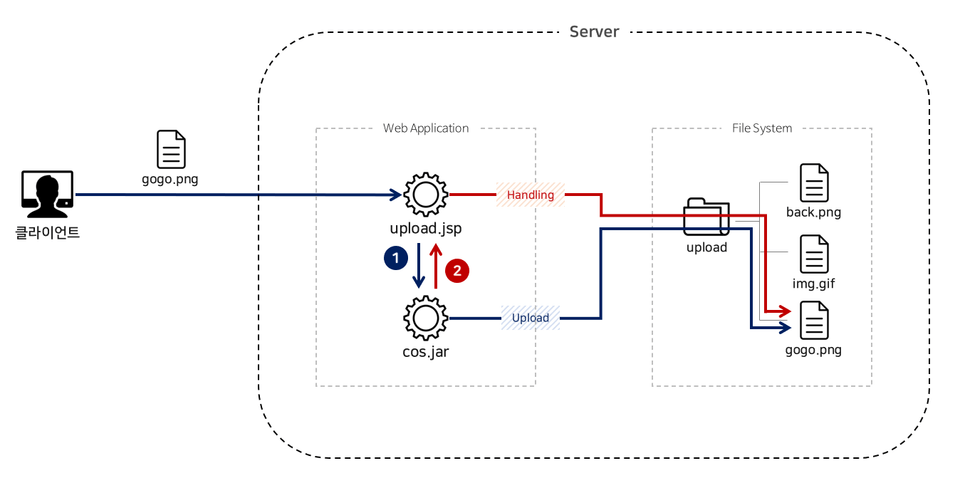
The source code below is known to be safe from file upload vulnerabilities. So is it really safe?
... String path = request.getRealPath("/upload"); MultipartRequest multi = new MultipartRequest(request, path, 1024*10*10, "UTF-8"); Enumeration formNames = multi.getFileNames(); while(formNames.hasMoreElements()) { String param = (String)formNames.nextElement(); String uploadFile = multi.getFilesystemName(param); int extOffset = uploadFile.lastIndexOf("."); String fileExt = uploadFile.substring(extOffset+1).toLowerCase(); if (!fileExt.equals("jpg") && !fileExt.equals("png") && !fileExt.equals("gif")) { File fp = new File(path, uploadFile); fp.delete(); out.println(“ "); return; } } ...<script> alert(‘잘못된 확장자’);history.back(-1);</script>... String path = request.getRealPath("/upload"); MultipartRequest multi = new MultipartRequest(request, path, 1024*10*10, "UTF-8"); Enumeration formNames = multi.getFileNames(); while(formNames.hasMoreElements()) { String param = (String)formNames.nextElement(); String uploadFile = multi.getFilesystemName(param); int extOffset = uploadFile.lastIndexOf("."); String fileExt = uploadFile.substring(extOffset+1).toLowerCase(); if (!fileExt.equals("jpg") && !fileExt.equals("png") && !fileExt.equals("gif")) { File fp = new File(path, uploadFile); fp.delete(); out.println(“ "); return; } } ...
No , the source code is 'vulnerable' .
Why this code is vulnerable and how to exploit it are covered in detail in lecture Part 2-1.
Understanding Cases by File Upload Library
We analyze each file upload library, covering potential security threats and different cases that can occur.
Methodology and Practices for Security Threats
We explore potential security threats and practice attacks for a variety of cases.
'File Upload Vulnerability Part 2' consists of three lectures to successfully attack file upload vulnerabilities in various environments. However, this is not a lecture that gives you the right answers. Taking this lecture does not mean that you will successfully attack file upload vulnerabilities in all environments.
The goal of this lecture is not to give you the right answer, but to broaden your perspective . If you learn that vulnerabilities can occur in various environments, you will gain the enlightenment of 'Oh, I can try this too!', and furthermore, you will be able to 'know' and analyze various environments in future diagnoses. There is a world of difference between knowing and analyzing this and analyzing without knowing.
I hope that this lecture will give you a solid perspective on web hacking and lay the foundation for taking your skills to a higher level!
Q. Is there anything I should know before taking the course?
You must have an understanding of 'File Upload Vulnerability'. Additionally, if you know the content covered in Part 1 , you will be able to take Part 2 smoothly. Of course, if you have a high level of understanding of 'File Upload Vulnerability', you will not have a problem taking the course.
Q. Who is eligible to take the course?
I recommend that 'practitioners' take this course as much as possible. Or, those who have sufficiently studied the theory of web hacking, or those preparing for employment can also take this course.
Q. Do I have to take 'File Upload Vulnerability Attack Part 1' ?
I recommend that you take this course. Even if you understand file upload vulnerabilities, if you do not understand Part 1, there will be parts of Part 2 that you will not understand. Therefore, even if you are a practitioner, I recommend that you take Part 1 first and then Part 2.
Q. Part 2 is divided into 3 parts. Do I have to take them all?
You don't have to take all three. However, if you want to learn attack methodologies for various practical environments, I 'strongly' recommend taking all three.
Q. Should I take Part 2 in the order of Part 3?
You don't have to do that, and you can take the ones you want first. However, since the three lectures were produced in order, it would be better to take them in order.
We recommend that you take this course with an understanding of web technology and web hacking. We also recommend that you first take the lectures ‘File Download Vulnerability Attack’ and ‘File Upload Vulnerability Attack Part 1’ from Creative’s web hacking lecture series.
Who is this course right for?
Practitioners who perform simulated hacking or vulnerability diagnostics in the field
job seeker
Need to know before starting?
web technology
Web Hacking Basics
File Download Vulnerability Knowledge
File Upload Vulnerability Knowledge
26,521
Learners
1,436
Reviews
504
Answers
4.9
Rating
18
Courses
안녕하세요, 크리핵티브입니다.
다년간 다양한 웹 서비스를 진단하고 연구한 경험을 바탕으로, 실무에 바로 적용 가능한 지식을 인프런 플랫폼에서 공유해오고 있습니다.
그리고 웹 해킹 기초를 체계적으로 다룬 『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』을 집필했습니다. 기초가 부족한 분들께는 이 책으로 학습을 시작하실 것을 권합니다.
『크리핵티브의 한 권으로 끝내는 웹 해킹 바이블』 저자
이메일 : crehacktive3@naver.com
All
31 lectures ∙ (2hr 24min)
Course Materials:
All
4 reviews
5.0
4 reviews
$34.10
Check out other courses by the instructor!
Explore other courses in the same field!