
AWS 클라우드 서비스 인프라 구축 이해와 해킹, 보안
보안프로젝트
IT 서비스가 클라우드 환경으로 빠르게 전환되고 있습니다. 아마존 AWS 클라우드 환경 보안을 위해 알아야 할 기본적인 가상 인프라 구축부터, 각 영역별 보안 위협 모니터링, 취약점 진단 관점을 통해 보안 실무를 배우게 됩니다.
초급
AWS, 모의해킹
IT infrastructures are being moved to virtualization and cloud environments. Services are becoming more diverse, and many applications are being operated on the infrastructure. In order to respond to the security of increasingly complex infrastructures, various security devices are being introduced. However, this will be a lecture where you can sufficiently practice and prepare using open tools for things that you cannot experience without purchasing security devices.
Building IT security infrastructure
Understanding vSphere Hypervisor
Building infrastructure using ESXi
Security Control Work + Infrastructure Construction Basics! 🚧
In a VMware ESXi (vSphere Hypervisor) virtual environment
Reflecting the introduction and practice of security systems
Build networks and infrastructure
Ability to monitor security threats
The perfect guide!
IT infrastructure services are moving to virtualization and cloud environments. Services are becoming more diverse, and many applications are operating on the infrastructure. In order to respond to the security of increasingly complex infrastructures, various security devices are being introduced. However, this will be a lecture where you can sufficiently practice and prepare using open tools for things that you cannot experience without purchasing security devices.
Through this lecture, you can build a security infrastructure like the above. You will directly configure a miniature version of the infrastructure structure that is being operated in practice in a VMware ESXi virtual environment, and learn how to integrate logs and detect abnormal signs of attacker attack patterns .

Corporate Security Jobs
Job seeker

Security Officer as a Newcomer
The person in charge of the work

Virtualization environment infrastructure
For those who want to understand better

Close to the practical environment
Anyone who wants to try the practice
The infrastructure security lecture uses a virtual environment to configure the security solution equipment used in practice in software. Since it is an optimized practice that individuals can do compared to the practical environment, if you understand this lecture, you will not have much difficulty even if you immediately start a practical project.
This course is necessary for everyone, from students preparing for employment in security control, breach analysis, and security personnel at large companies/financial institutions, to those who are new to related work . Even if you later switch to cloud services, you will have difficulties if you do not understand the existing virtualization environment infrastructure.
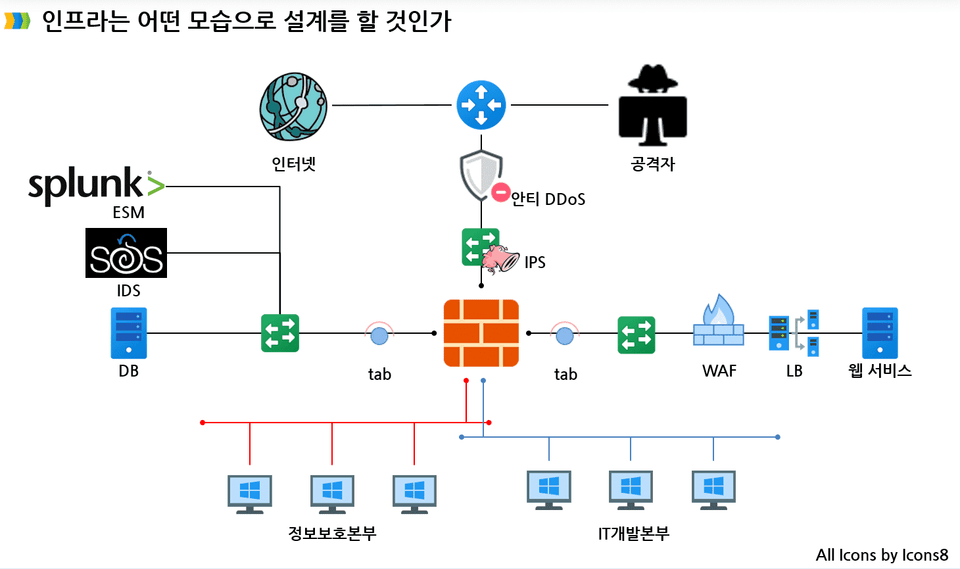
In the infrastructure security lecture, we will create a network structure similar to the actual work as shown below and proceed to the process of detecting attack patterns with an integrated log system . In addition, we will guide you on how to directly respond to attack patterns and block them in the network system.
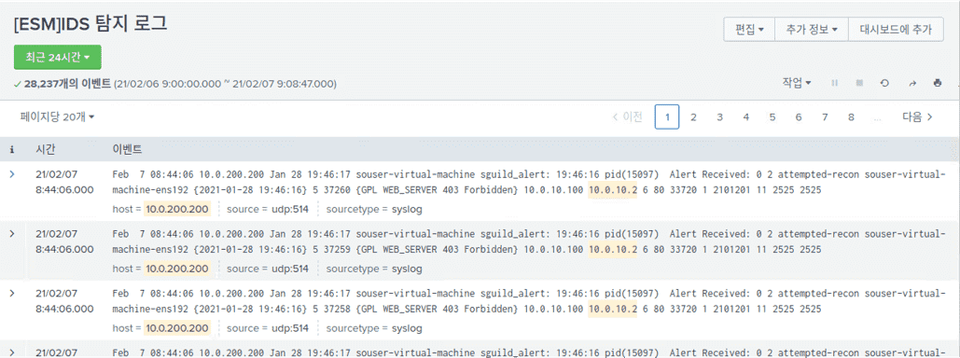
We will collect and analyze both attack logs and abnormal symptom logs using Splunk, the most widely used integrated log system in practice.
The lecture will be given directly by an instructor who has obtained cloud service expert certifications such as AWS, GCP, and Azure. We will guide you so that you can accurately understand the infrastructure of the on-premise virtualization environment before switching to a cloud environment .
Please make sure to check before taking the class!
Security Project - Frontline CTO
- Security Project Online Lecture General Manager
- Multi-campus IT external expert instructor (Kubernetes, bug hunting, etc.)
- Caseyd Junior External Professional Instructor
- Hansae Cyber, Dongil Industrial High School Cyber Guardians external expert instructor
- Establishment and development of hacking defense system
- Long-term course on “Breach incident analysis and ELK integrated log system construction”
- Long-term course on “Data Analysis Utilization”
- Long-term course on “malicious code analysis by type”
- Author of Perfect Practice in Web Mock Hacking Using Vibox
- Online lecture on building and utilizing ELK integrated log system for IT professionals
- Windows Application Vulnerability Analysis Online Course
- About 30 lectures including “Introduction to Network Packet Analysis and Malware Sample Analysis”
Who is this course right for?
Anyone who wants to understand IT security infrastructure
Anyone who wants to understand the security control work system
Those who have chosen a career in IT security
Anyone looking to move to a security position
Need to know before starting?
Understanding Virtual Environment Systems
Understanding the operating system
Understanding Security System Terminology
101,692
Learners
3,143
Reviews
445
Answers
4.7
Rating
67
Courses
보안프로젝트 ( www.boanproject.com )는 IT보안, 빅데이터, 머신러닝, IoT 등 다양한 분야의 온라인 강의, 그룹 강의를 진행하고 있습니다.
All
63 lectures ∙ (12hr 57min)
Course Materials:
All
44 reviews
4.8
44 reviews
Reviews 22
∙
Average Rating 5.0
Reviews 1
∙
Average Rating 5.0
Reviews 2
∙
Average Rating 4.0
Reviews 2
∙
Average Rating 5.0
Reviews 5
∙
Average Rating 5.0
$152.90
Check out other courses by the instructor!