
Memorize and finish the core network theory - Basics
nullnull8537
From TCP/IP to HTTP! This lecture is for those who lack basic network theory and want to understand major theories by memorizing them. You can do it!
Beginner
Network, Protocol
We will help you memorize and finish the encryption technology responsible for the security of the Internet very easily. You can understand the structure and principles of various technologies such as SSL certificates, PKI technology, digital signatures, and public authentication systems.

Conceptual structure and principles of cryptography
Cryptographic technology used in all areas of IT technology, including symmetric keys, asymmetric keys, and hashes
Structure of SSL authentication system applied to web services
Structure and operation of public certificate
PKI technology and digital signature principles
Cryptography, don't learn it the hard way!
You can quickly memorize it and finish it within 2 hours.
It is the core of various security technologies such as VPN, SSL certificate, and public certificate.
To truly understand how complex cryptographic technologies work, it's essential to understand PKI technology in general.
PKI technology is central to all security technologies, including personal information protection. It's utilized in all fields, from network security technologies like VPNs to SSL certificates. SSL certificates and public key certificates are already closely intertwined with our daily lives. Even for those who aren't developers or system engineers, the need to understand related theories is growing.

In fact, PKI is already deeply ingrained in our daily lives. Most web services these days communicate via HTTPS, not HTTP. To understand why HTTPS requires SSL communication and how it works, we must ultimately understand PKI technology in general.
Such cryptography techniques are complex and difficult to learn, involving complex mathematics. This is why many people hesitate to learn. However, if you ignore the complex formulas and focus on the structure and principles, it's not difficult at all.
😵
Anyone who wants to easily understand complex cryptographic technologies such as SSL and PKI.
🥺
Systems engineers, developers, and IT practitioners who desperately need an understanding of cryptography.
💡
You should have a basic understanding of arithmetic operations , binary ↔ hexadecimal conversion , and the structure of web services .
This lecture provides an overview of PKI technology in a simple, no-frills manner. While the theory may be daunting and complex, memorization alone will allow you to achieve a certain level of understanding. We aim to help anyone, even those with a computer science background, easily understand cryptography and the core principles of PKI!
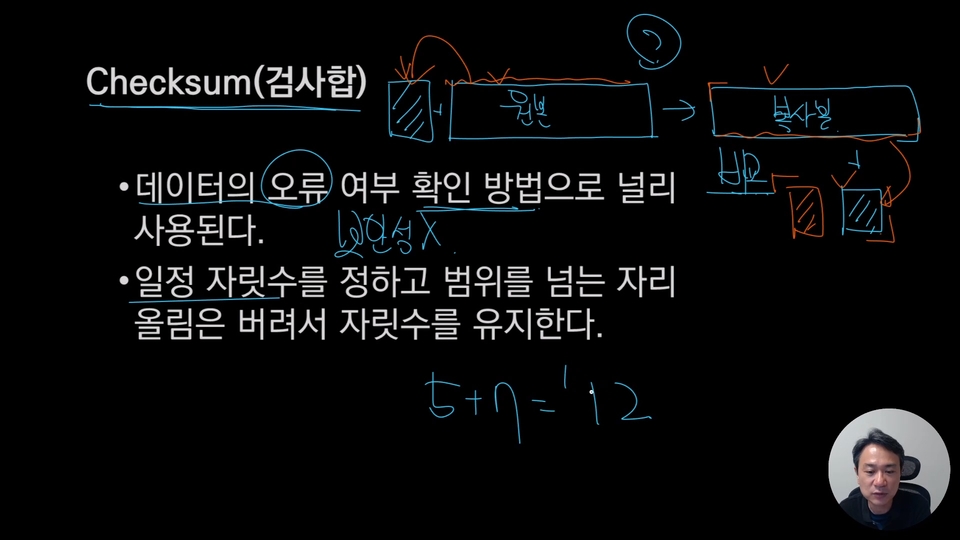
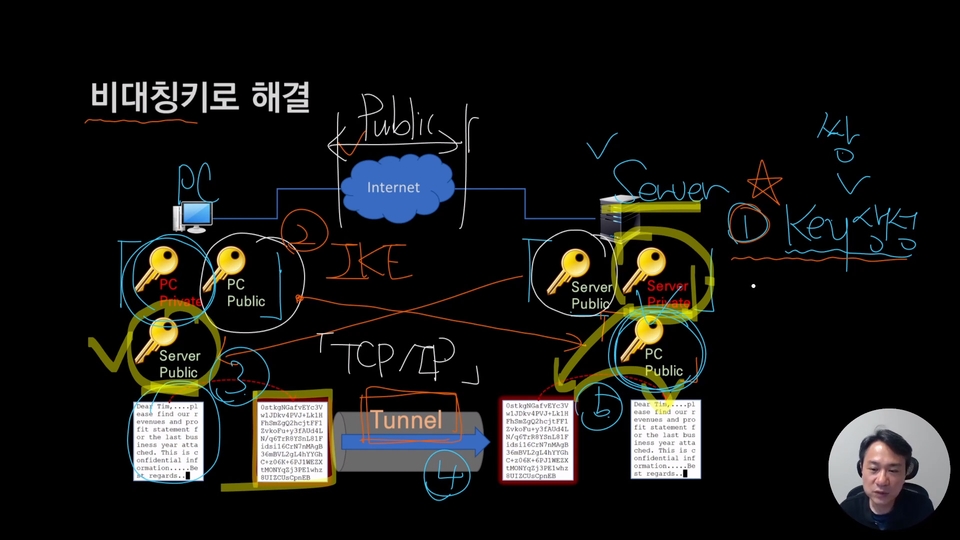
Complex encryption? No need to go back to the trouble. 😊
SSL and PKI are widely used technologies. However, I often see people hesitant to learn them due to the burden of cryptography. However, having a basic understanding of these cryptographic technologies, which protect information within the open environment of the Internet, will provide a powerful weapon for IT professionals .
The goal of this course is to enable you to memorize and understand these concepts without any burden . I hope many of you will be able to quickly and easily complete the core principles of Internet security in a short amount of time!
Who is this course right for?
Operator who manages the web service system
Developers who want to know the structure and features of SSL certificates
IT professionals or students interested in PKI technology
Need to know before starting?
Binary to Hexadecimal Conversion
Ability to perform logical operations (especially XOR) and arithmetic operations
45,774
Learners
2,573
Reviews
1,144
Answers
4.9
Rating
25
Courses
All
11 lectures ∙ (1hr 51min)
Course Materials:
All
170 reviews
4.9
170 reviews
Reviews 19
∙
Average Rating 4.9
5
I have completed the course. Regarding SSL, I only knew about determining whether a certificate is trustworthy by Googling the public key of the CA installed on the PC, but I have a chance to properly learn about the organizations related to certificates, such as symmetric key ~ asymmetric key ~ hybrid method ~ PKI authentication system flow. Thank you. --------------------------------------- For your information, the tuition fee of 44,000 won for this course is not expensive for students compared to the class time. For those who are taking the course, I recommend subscribing to the instructor's YouTube channel and visiting the community, where the instructor gives out coupons for his lectures every month, and using the coupons to receive a discount and take the course.
Thank you for your good evaluation and specific feedback. Also, thank you for the information for students. I will continue to upload coupons for students in the future. ^^
Reviews 8
∙
Average Rating 4.8
5
I am a student. I was assigned to the authentication and authorization part of the web service team project, so I wrote the code using the jwt token method. Since I followed someone else's code without understanding it, I searched for various videos to understand it, but I wasted time. This lecture is the answer. It is not important to have a jwt token or a jwt data structure, but the concept of cryptography. (Even if you don't know terms like jwt token or something, if you have a concept of cryptography, you will be able to understand it when you write the code.) The lecture title is "Memorize and finish", but the core concepts are explained very logically. "Memorize and finish" means "I will not prove it mathematically, but I will just organize the results and tell you." Anyway, I gained a lot of knowledge, and it was very fun. Maybe because the lecture title is cryptography, not many people seem to take it, but it is almost essential for developers to know.
PKI theory appears in all parts related to JWT or authentication systems. As you have given feedback, I personally hope that developers will watch this lecture. I am surprised and grateful that you have accurately explained that part. ^^
Reviews 81
∙
Average Rating 5.0
5
Thank you for the great lecture. I thought it was a difficult topic, but the analogy was so good that I could understand it easily.
As a teacher, I am very happy that you understood it easily. Thank you. ^^
Reviews 1
∙
Average Rating 5.0
5
Thank you so much for the great lecture!! I was implementing the login part while making an app, and I didn't understand what they were talking about, such as hash and public key, but you explained the entire flow, so I understood it so well!!
Thank you for your good evaluation. You are a developer! If you do not want to study complex cryptography theory mathematically, I expect that you will be able to utilize the APIs well just by understanding the contents of this lecture. ^^
Reviews 32
∙
Average Rating 5.0
5
This lecture is also very helpful for basic knowledge in understanding OAuth2. If I had watched this lecture and tried to understand JWT's RS256 algorithm and JWK, I think it would have taken a lot of time. Thank you for the great lecture.
Thank you for your first class review. I am glad that you found it helpful. I will continue to make better lectures. And I will also add more content to this lecture. Thank you. ^^
Limited time deal ends in 8 days
$30,800.00
30%
$34.10
Check out other courses by the instructor!
Explore other courses in the same field!