AI-Driven Practical Application Strategies in Manufacturing (Construction/Civil Engineering Fields)
88888
$51.70
29%
$36.30
Beginner / AI, Generative AI, Big Data, Machine Learning(ML), Deep Learning(DL)
This course is a specialized program that covers practical application strategies for utilizing artificial intelligence (AI) in the construction and civil engineering fields. In the construction industry where digital transformation is accelerating, AI is driving innovation across design, construction, safety, and quality management. This course focuses on learning practical application cases that can be utilized in actual field sites, including smart construction, digital twins, AI-based equipment control, safety monitoring, and quality verification.
Beginner
AI, Generative AI, Big Data





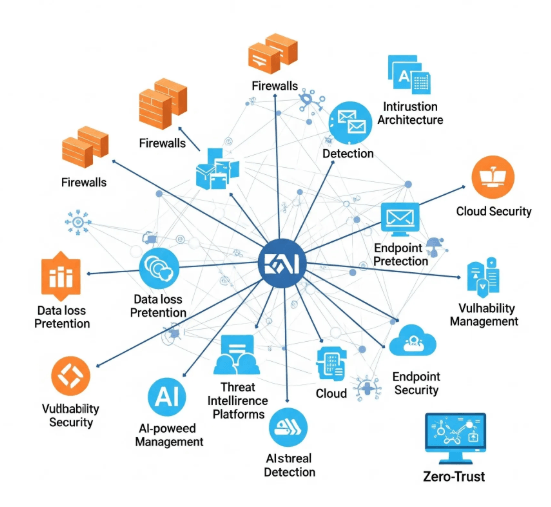

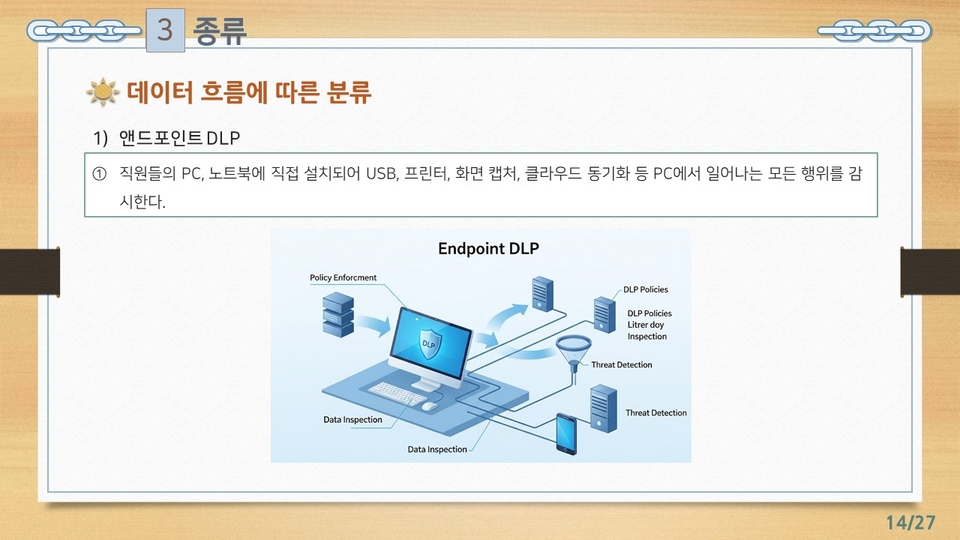

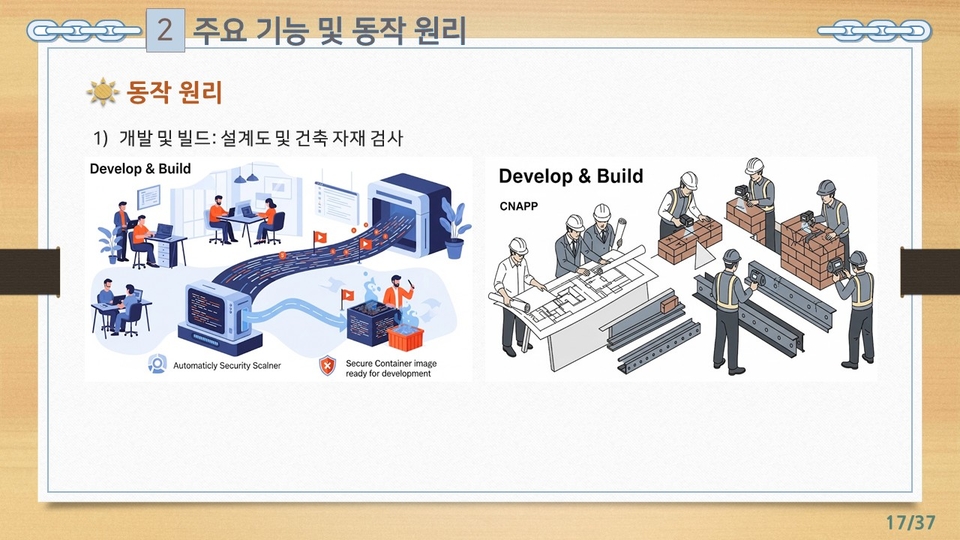
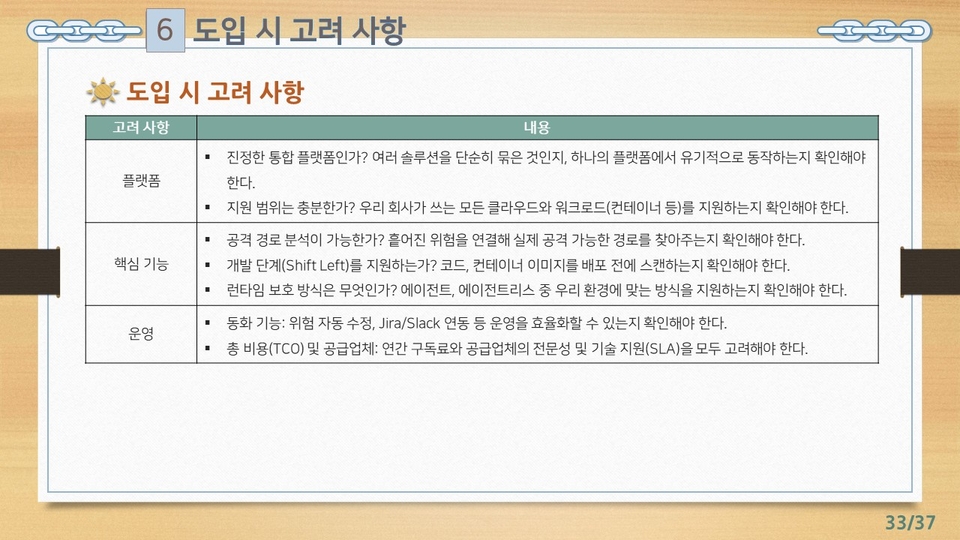








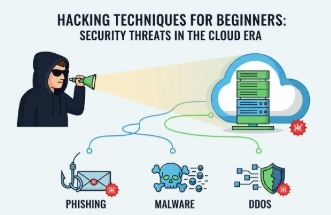
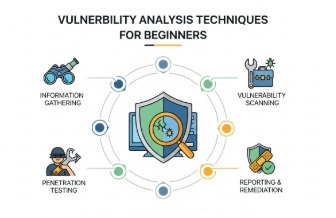





![[Certification Preparation] Test of Information Security Literacy (TOLIS)Course Thumbnail](https://cdn.inflearn.com/public/files/courses/335790/cover/01k1fkg3ge5sb67f0xdtesh791?w=420)